The future of the American workplace is hybrid. As the world slowly pieces itself back together in the wake of the COVD-19 pandemic, everyone is wondering what’s coming next in terms of the environments we work in every day.
Some want to continue working remotely, while others foresee a return to in-person office work. However, many more are shifting focus to a hybrid working model, in which certain days of the week feature in-person work at an office or site, and the rest of the week is remote.
There are many benefits to switching things to a hybrid model from an employee perspective. It allows for more flexibility, people will save money on commuting costs like fuel, food, and childcare, and it will improve the all-important work-life balance.
However, for security experts, hybrid work creates a slew of vulnerabilities. When employees work outside the office, their devices and the precious company data stored within become vulnerable to attack. It’s possible that connecting to a public Wi-Fi hotspot or downloading Malware-infected files could put the entire company at risk.
But there are ways to tighten security around your workplace and ensure that your switch to remote work doesn’t leave the entire company open to cyberattacks.
In this article, we will explore four best practices for data security in a hybrid working environment.
Strengthen Your IT Infrastructure
If your business uses complex data infrastructure management software, you’ll have to consider how that will work as you transition to a hybrid model.
It may be necessary to add to your software to ensure that it continues running properly for hybrid teams. CMDB software is a popular remedy for the potential issues caused by complex data infrastructure management software.
Using CMDB, you can simplify your security measures, eliminate inconsistent data, and boost data accuracy throughout your entire system.
CMDB stands for Configuration Management Database, and it contains all of the information on the hardware and software you’re using. It keeps track of every component that makes up your IT infrastructure.
By connecting your DCIM software with CMDB, you’ll improve data accuracy and simplify all your data center security management practices. You’ll be able to keep track of everything better and identify potential security problems before they cause issues.
Of course, when moving on to implement data security guidelines for your hybrid team, it’s also important to ensure that your data pipeline architecture is strong enough to support any data inputs and avoid breaches.
Your data pipeline enables the transfer of data from a source platform to a destination. So a breach in the line would prove catastrophic for data security. To ensure that your pipeline is strong, you should understand who has access to it and what their jobs and permissions are while keeping the system up to date.
One way to ensure that your data is secure is to use some of the most advanced military-grade encryption in the world. While this might sound expensive and complicated, it’s not.
Use Encryption
When employees work with sensitive data outside the workplace, you have to make sure that their devices are protected.
That’s why it’s important to encrypt your data and secure your network.
One of the easiest ways to encrypt internet traffic is using a high-grade VPN service like ExpressVPN or NordVPN.
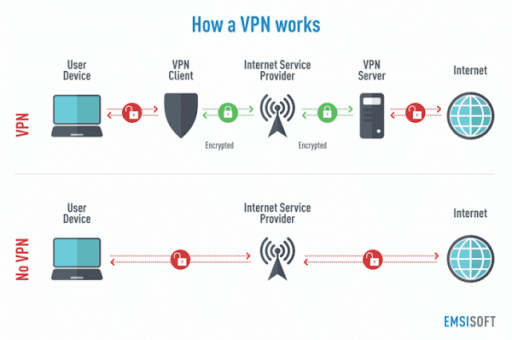
VPN stands for Virtual Private Network, and it’s a security system that allows you to browse the internet anonymously by tunneling your connection through an encrypted tunnel to a server located somewhere else.
Most top VPNs on the market today use AES-256 encryption. This is the most powerful encryption in the world. It would take the world’s most advanced supercomputer over one million years to crack it.
Suffice it to say, when you’re trying to keep your business’s traffic safe, using a VPN with this level of encryption can protect you.
Whenever a hybrid employee connects to company data, whether at home or (especially) on an unsecured public Wi-Fi network, they should first connect to a VPN to ensure that no malicious actors or cybercriminals can gain access to your company’s secrets.
Keep Your Team Educated
You don’t want to implement security measures and keep your team in the dark about them. One of your most glaring vulnerabilities will be the security practices of your remote staff. The best way to close up that vulnerability is by keeping staff members educated on what you’re doing to improve security and what you expect of them.
After all, if your employees don’t understand the measures you expect them to take, they can’t be held accountable when they make a mistake.
Before adopting a hybrid work model, hold a training session with your team to go over the dos and don’ts of data security. Show them how to securely access the network, log in to your VPN, set up multi-factor authentication, and then test them on it.
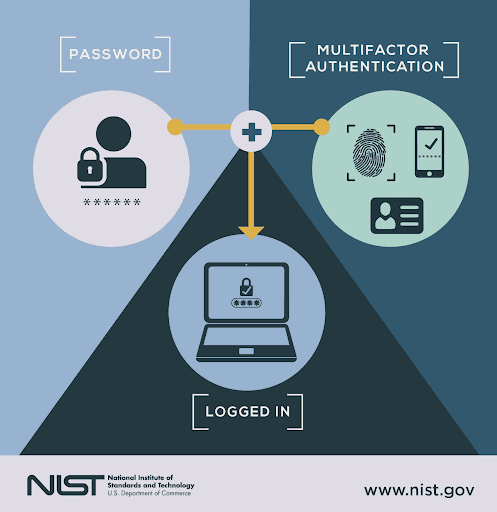
Once they’ve passed a competency test, you’ll be able to hold them accountable for any issues they might cause.
Once the hybrid environment has been established, security training should become a part of new employee onboarding conducted as part of your HR management processes.
Adopt Zero Trust Model
While this concept might seem a little extreme, the Zero Trust Model has gained popularity as the hybrid work world begins to rise.
Zero Trust is exactly what it sounds like. No devices or users are ever fully trusted, even if they’re logging in on-site to the company network. Your employees will have to re-do an authentication process every time they log on.
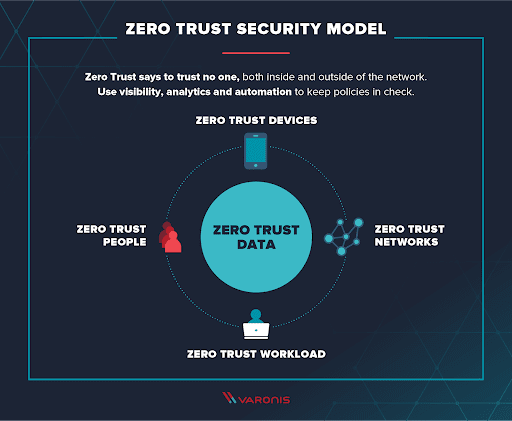
They’re also given the lowest amount of access needed, with no excess access granted anywhere in the company. This is known as the Principle of Least Privilege, and it ensures that no one has access to anything they don’t need.
This principle extends beyond human team members and even keeps systems and devices limited to only the permissions they need to perform specific tasks.
Wrap Up
By implementing these four best practices, you can ensure that your data security is top-notch as you move forward into the exciting world of remote workspaces.
To review: you can strengthen your IT infrastructure, use encryption in the form of a VPN, keep your team educated as to what’s expected of them, and adopt a zero trust model to make sure that no one has too much access to your system.
Hybrid work is here to stay, but you can make the transition easier by ensuring that your data has maximum protection.
 Author Bio
Author Bio
Joanne Camarce is a digital marketer focused on growing and strategizing B2B marketing and PR efforts at uSERP. She loves slaying outreach campaigns and connecting with brands like G2, Wordstream, Process Street, and more. When she’s not wearing her marketing hat, you’ll find Joanne lost in the world of Japanese music and art, or just being a dog mom.