In the race for digital dominance, speed and security are often treated as opposing forces. Developers want to push code faster, while security teams want to slow down to ensure safety. However, the rise of the “Secure-by-Design” philosophy has proven that you can have both—provided you have the right infrastructure and automated oversight.
To achieve this balance, forward-thinking organizations are adopting a dual-pillar strategy: leveraging DevOps Managed Services for operational agility and implementing Advanced Cloud Vulnerability Management for proactive defense.
The Operational Backbone: DevOps Managed Services
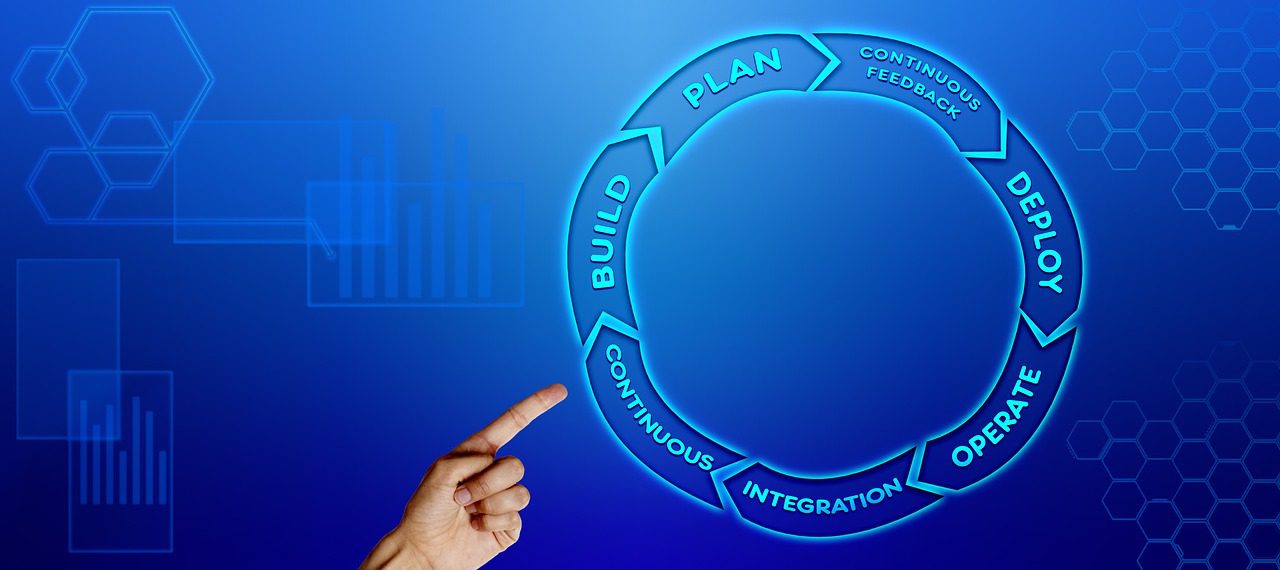
The complexity of modern cloud-native environments—utilizing Kubernetes, microservices, and multi-cloud architectures (AWS, Azure, GCP)—has made “DIY DevOps” a risky and expensive endeavor. This is where DevOps Managed Services, such as those provided by Opsio Cloud, become a game-changer.
By partnering with a managed service provider (MSP), businesses offload the burden of maintaining CI/CD pipelines, Infrastructure as Code (IaC), and 24/7 monitoring. This allows internal teams to focus on innovation rather than troubleshooting environment drift. A managed approach ensures:
- Infrastructure Consistency: Eliminating manual configuration errors that lead to downtime.
- Cost Optimization: Scaling resources dynamically to prevent “cloud sprawl.”
- Rapid Deployment: Accelerating the journey from a developer’s laptop to a production environment.
The Defensive Shield: Cloud Vulnerability Management
Operating a fast-moving pipeline is useless if it’s delivering vulnerable code. Traditional security audits, which often happen at the end of a release cycle, create massive bottlenecks. Modern Cloud Vulnerability Management solves this by “shifting left.”
Platforms like SeqOps integrate directly into the DevOps workflow. Instead of waiting for a quarterly scan, security becomes a continuous, automated process. Key features of a high-maturity vulnerability program include:
- Automated IaC Scanning: Detecting misconfigured security groups or unencrypted databases before the infrastructure is even provisioned.
- Software Composition Analysis (SCA): Identifying vulnerabilities in third-party libraries and open-source dependencies (e.g., Log4j-style risks) in real-time.
- Contextual Prioritization: Using AI to filter through thousands of alerts and highlighting the 5% that actually pose an immediate threat to your specific environment.
Synergy in Action: The DevSecOps Ecosystem
When you combine professional DevOps management with automated vulnerability tools, you create a self-healing ecosystem. For example, if a new vulnerability is detected by SeqOps, a managed service provider like Opsio Cloud can immediately deploy an automated patch through the existing CI/CD pipeline, often before the security team even has to manually intervene.
This synergy is particularly critical for sectors with high compliance requirements, such as BFSI (Banking, Financial Services, and Insurance) and Healthcare. Automated reporting and audit trails ensure that the organization remains “audit-ready” every day of the year, not just during inspection periods.
Final Thoughts
The future of cloud computing belongs to organizations that can innovate without fear. By investing in DevOps Managed Services to handle the operational “how” and Cloud Vulnerability Management to handle the security “what,” enterprises can finally achieve the ultimate goal: high-velocity software delivery that is inherently secure.
Don’t let your infrastructure become your bottleneck. Embrace automation, unify your teams, and build a digital foundation that is both agile and impenetrable.