Businesses of all sizes are constantly at risk from cybercriminals in today’s digital environment. Every company now has dozens, if not hundreds, of connected endpoints due to the growth of remote work, cloud computing, and mobile devices. Any of these devices could be compromised by hackers.
For security, a conventional perimeter is no longer sufficient. Attackers now target specific devices, such as laptops, smartphones, and even Internet of Things devices, to obtain sensitive business data. Because of this modification, endpoint security is now a crucial component of any contemporary cybersecurity strategy.
Cyber Threats That Change
Cyberattacks are no longer random or opportunistic but fine-tuned, targeted and innumerable. To break through security, hackers would prefer to penetrate through laptops, smartphones, and IoT devices because they are among the most vulnerable to obtain security access. Exploiting vulnerabilities at endpoints may result in ransomware attacks, phishing scams, and zero-day attacks.
Attack surface has grown ever larger with remote and hybrid work increasing the number of avenues hackers use to enter. Without powerful endpoint protection, businesses are opening the door to hackers with a wide-open front door. Here, endpoint security has a crucial role, providing detection, policy enforcement and real-time automated response to secure all networked devices in your organization.
Common Cyber Threats to Business Endpoints
- Malware and ransomware attacks:
Malware is still one of the most common threats to endpoints. Ransomware is a type of malware that locks up business data and asks for money to unlock it. A single compromised laptop can infect the entire network of a company, which can stop business and cost a lot of money.
Phishing attacks trick employees into giving away their login information or clicking on bad links. If someone gets into a company’s cloud or email account, they could steal private information or pretend to be an employee to carry out more attacks. Phishing attacks often start at endpoints, especially personal laptops and smartphones.
- Unauthorized Entry and Internal Threats:
Not all threats come from outside. Contractors or employees may misuse access, either on purpose or by accident. An insider abusing privileged accounts or a misplaced device that isn’t properly encrypted can make private company information public. Access controls, monitoring, and encryption are some of the ways that endpoint protection solutions lower this risk.
- Important Parts of Endpoint Protection:
Not all endpoint protection features are equally important to businesses. Some of these are more important for stopping attacks, while others give you the visibility and control you need to be strong over time. The chart below shows how important each feature is based on how well it protects business endpoints. This will help you understand how they affect things.
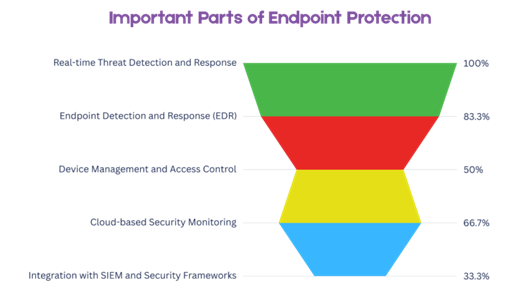
Caption: Important Parts of Endpoint Protection for a Company
Business Advantages of Endpoint Protection
Keeping the business going
Being down today means losing money and hurting your business’s reputation. For example, ransomware attacks can stop work for days or even weeks. Endpoint protection keeps devices safe, up to date, and free of viruses and other malware. This lets companies keep going even when there are cyber threats. Not only do you need to avoid problems, but you also need to make sure your business can handle anything in a digital-first world where customers expect to be able to reach you at any time.
Long-Term Savings
You might think that endpoint security is a waste of money, but it’s a way to save money. According to IBM’s 2024 Data Breach Report, the average cost of a data breach is now $4.45 million. These costs include paying lawyers, paying fines to regulators, losing customers, and getting the system back up and running. On the other hand, endpoint protection solutions are much cheaper. Because it reduces the likelihood of a breach, preventive security is not only a wise investment but also a necessity.
AI and automation for finding advanced threats
Hackers are using AI and automation to speed up and make their attacks more flexible. Businesses need to do the same. Basic antivirus software is only one aspect of modern endpoint protection. Additionally, it features automated response systems like MDR (Managed Detection & Response) and EDR (Endpoint Detection & Response), behavioral analytics, and threat detection driven by AI. These tools can detect suspicious activity quickly, halt attacks before they spread, and even repair compromised devices. This cutting-edge technique gives businesses a means of retaliating against cunning hackers. The Zero Trust Security Model
“Trust but verify” doesn’t work in the world of cybersecurity anymore. Companies are using Zero Trust instead. This means that all requests for access, whether they come from inside or outside the network, are checked all the time. This method relies heavily on endpoint protection, which makes sure that only secure devices and trusted users can get to sensitive resources. Getting rid of blind trust makes it much less likely that attackers will be able to get in and move around without permission.
How to Make Your Business Scalable
As a business grows, so does its digital footprint. There are new security holes in new offices, mobile devices, cloud apps, and IoT devices. Endpoint protection services are designed to grow with your business so that they can keep everything safe, from the laptops of a small startup to the computers of a global company with employees all over the world. Endpoint protection grows with a business, whether it hires more people or uses new technologies. This protects all devices and places all the time.
Security Culture and Employee Awareness
Employees are just as important as technology when it comes to keeping cyber threats at bay. Many endpoint protection services now have features that help people be more aware, such as alerts for phishing attempts, reminders to keep passwords safe, and training modules on security. This lets employees be the first line of defense instead of the weakest link. A strong security culture not only lowers risk, but it also makes it so that everyone at work is responsible for keeping company data safe.
Edge in the Market
Cybersecurity isn’t just something that happens in the background anymore; it’s a way to make your business stand out. Customers and partners of the business want to know that their information is safe. Companies that have good endpoint security not only lower risks, but they also gain trust and credibility in the market. In fields where there is a lot of competition, being able to show that you have good cybersecurity practices can help you get new clients and keep old ones.
In conclusion, businesses can no longer choose whether to use endpoint protection services; they must use them. By protecting their endpoints, businesses can lower the risk of breaches, stay compliant, boost employee productivity, and protect their financial stability.