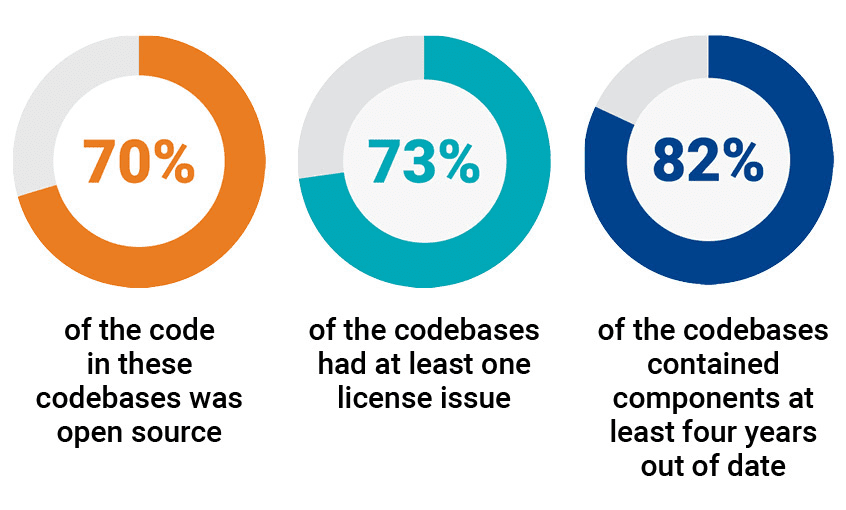
Open source software carries a number of concerns, including known and public vulnerabilities, the lack of a warranty or other software guarantees, and the possibility of sudden development halts. Therefore, it must be carefully examined because it also carries the possibility of development inadequacies and malpractices.
Risks of Not Managing Open Source Inventory
Any business must value its inventory. Both excessive and surplus inventory can seriously jeopardize a company’s flow and threaten its liquidity. Inventory optimization is essential to guarantee your stocks’ dependability and availability. It may minimize commercial risk. You may better oversee your company’s inventory management process by using an effective system of open source inventory management software. A computerized system is used to manage and track the quantity of products that are stored. Supply chain management includes a significant amount of inventory management.
Keeping track of your inventory of open source software components is crucial to the success of any software development project. Failure to manage your inventory can lead to a number of problems, including:
Risks of Non-compliance
Using open source software components without adhering to their specific licensing requirements can result in legal risks for your organization. For instance, the GNU General Public License (GPL) requires that any derivative works be distributed under the same license. Therefore, if you incorporate GPL-licensed code into your proprietary software and fail to distribute your software under the same license, you could be sued for non-compliance.
Similarly, the Apache License 2.0 mandates that you give credit to the original authors of the licensed software. Neglecting to do so could result in a lawsuit or penalty. To avoid such legal risks, developers and organizations must carefully review the licenses of open source components they use and ensure they meet all the necessary obligations.
Maintenance Issues
Regular maintenance and updates are required for open source software components. If you don’t manage your inventory, you risk missing essential upgrades or failing to discover and resolve issues, which can lead to software failures and downtime.
Security Threats
Using outdated and vulnerable open source software components can expose your system to security threats. For example, in 2017, the widely-used open source library Apache Struts was found to have a critical security vulnerability that allowed hackers to remotely execute code on affected servers. This vulnerability was exploited in the Equifax data breach, which compromised the personal information of over 143 million individuals.
If you use an outdated version of Apache Struts or fail to update it to the latest version, your system may be vulnerable to this security threat. Therefore, it is critical to regularly check and update all open source components used in your system to ensure they are secure and up-to-date. Adopting continuous security testing and monitoring practices can also help identify and address any security threats.
Risks of Incompatibility
Open source software components are often derived from diverse sources and may lack compatibility with one another. Inadequate inventory management may cause conflicts between different components, thereby compromising program stability and inducing faults.
What Are the Other Open Source Software Security Risks?
There are various causes for open source vulnerabilities and dangers. In essence, vulnerabilities result from shoddy programming that invites assaults and exploits. These, however, are compounded by OSS-related issues, which must be taken into account. The main causes of open source security issues are listed below.
Operational Risks
Locating the latest patch or repair for open source components can sometimes pose challenges. It is crucial to perform routine maintenance and update all open source components to their latest version to prevent any vulnerable gaps in the system. For efficient inventory management, businesses should automate the process of keeping track of open source components.
Another operational risk is having to patch vulnerabilities in abandoned projects that no longer receive community support. To mitigate such risks, businesses need to allocate personnel and funding for monitoring these projects and ensuring their secure management.
No Warranty and Security Guarantees
There might not be any security assurances, warranties, or support for open source software. Open source development is frequently a voluntary endeavor, and projects may be closed or abandoned if developers fall behind. This implies that appropriate testing during the development phase may or may not have taken place. Community members frequently offer some testing and support, but they can’t be depended upon to have found every potential problem.
Development Insufficiencies
Participating in the open source ecosystem occasionally results in the persistence of certain development errors and deficiencies. Poor habits, such as copying and pasting code, can expose vulnerabilities and make them difficult to find. For starters, any vulnerability already present in the code will be transmitted to your project when you copy and paste. However, once a code fragment enters your database, it cannot be modified or tracked, leading to potential vulnerabilities in the future.
Publicity of Vulnerabilities
Organizations, developers, and other members of the open source community publicly disclose vulnerabilities in their products. Prior notifications are sent to the community before vulnerabilities are made public, but this does not ensure that they won’t be used against you. Also, it does not imply that everyone will apply patches and updates on schedule. This discrepancy leaves vulnerable components exposed to exploitation and opens security gaps.
How to Prevent Open Source Security Risks and Vulnerabilities
Here are some open source security policies and processes you may take to reduce the dangers.
Create Comprehensive Policies
Rules should examine the history of an open source component, such as the density of known issues, the frequency of version releases, and the time lag between issue identification and patching. It is critical to understand the strength of the community involved in a project and to anticipate what kind of support it may or may not provide.
Emphasize Security-First
First and foremost, define and enforce a security strategy outlining the acceptable risk threshold when using open source libraries and components. Keep track of any open source software licenses, component histories, vulnerabilities, and updates that are currently in use.
Train Your Staff
To improve your security posture, train non-security personnel and increase communication between development and security teams. Ascertain that developers understand security vulnerabilities and how to detect and mitigate them.
Use a Binary Repo Manager
A binary repository manager is a must-have tool for anyone who manages open source components. Such technologies enable you to cache local copies of open source components, making commonly used packages available even when external repositories are unavailable.
Automate, Monitor, and Test
Use an automated security solution to monitor for vulnerabilities via logs, audits, incident notifications, and other means. All open source software should be thoroughly tested before and during its life cycle. For example, static analysis, which searches and tracks code, should be employed to provide security checks. Manual code reviews should be carried out where necessary.
Conclusion
In today’s development settings, open source software and components are critical enablers of agility. Almost many developers employ open source components in their apps, whether at the front or back end; there is a library for almost any stack you can imagine. Developers can use these components to make their work easier, which will allow them to focus on organization-specific difficulties, such as designing the key proprietary software features that provide value to corporate systems.