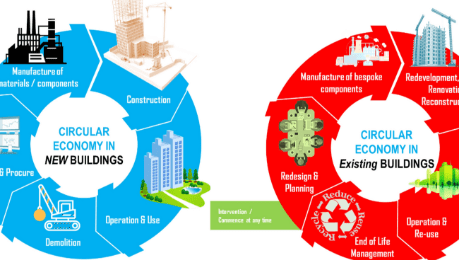
As the global economy transitions into a closed-loop system, a new vulnerability has emerged: the Digital Backbone of circularity. In 2026, Business resilience is no longer just about material recovery; it is about defending the hyper-connected “Circular Infrastructure”—the network of Digital Product Passports, IoT-enabled sorting facilities, and AI-driven resale markets—from a new generation of autonomous threats. We have entered the era of AI-Driven Cyber-Resilience, where the defense of the planet’s resources is inseparable from the defense of its data.
1. The Vulnerability of Connected Loops
The circular economy of 2026 relies on the “Sovereign Flow” of data across complex, multi-party ecosystems. This connectivity, while essential for sustainability, has expanded the attack surface for global threats.
-
Agentic Threats to the Supply Chain: 2026 has seen the rise of “Hacking Agents”—autonomous AI systems capable of probing circular networks for weaknesses at speeds that outpace human defenders. These agents can target the Digital Product Passports (DPP) of high-value components, attempting to “poison” the data to hide the origin of illicitly sourced materials.
-
Infrastructure Sabotage: As recycling and remanufacturing become central to national security, circular hubs are now classified as “Critical Infrastructure.” A cyber-attack on an automated sorting facility doesn’t just steal data; it physically halts the supply of recycled raw materials, creating immediate Business stagnation.
-
The “Vibe-Coding” Risk: The acceleration of software development through AI (often called “Vibe-Coding”) has led to rapid innovation but also to “Unsecured-by-Design” modules. In 2026, many circular platforms are racing to patch vulnerabilities inadvertently injected by the very AI tools used to build them.
2. Defensive Innovation: The AI-First Security Plane
To counter these risks, the Technology of 2026 has moved from “Detect and Respond” to “Deny, Deceive, and Disrupt.” Cyber-defense is now an automated, intelligent layer that permeates the entire enterprise.
-
Automated Moving Target Defense (AMTD): To make circular networks “Unreliable” for attackers, resilient businesses use AMTD. This Technology dynamically alters system parameters and network configurations in real-time, effectively “shifting the maze” so that an attacker’s plan becomes obsolete before it can be executed.
-
Predictive Vulnerability Management: In 2026, we no longer wait for a breach. AI-driven platforms use global telemetry to predict which security flaws are likely to be weaponized next. This allows management to deploy “Proactive Patches” to the circular infrastructure before an exploit is even released.
-
Identity Threat Detection and Response (ITDR): As 35% of cloud incidents now involve “Valid Account Abuse,” 2026 defense focuses on the user. ITDR uses Artificial Intelligence to monitor session behavior, detecting subtle “Lateral Movements” that indicate a compromised identity, and autonomously revoking access within seconds.
[Table: The Evolution of Cyber-Defense in the Circular Era]
| Metric | Legacy Security (2024) | 2026 Cyber-Resilience |
| Strategy | Reactionary (Post-Breach) | Proactive (Pre-Emptive) |
| Response Time | Minutes to Hours | Milliseconds (Autonomous) |
| Infrastructure | Static & Rule-Based | Dynamic & Moving Target |
| Compliance | Periodic Audits | Continuous & Automated |
3. Digital Marketing: Building the “Trust-as-a-Service” Brand
In a world of constant digital instability, Digital Marketing has pivoted to “Trust Management.” For the Sovereign Consumer of 2026, security is a non-negotiable feature of a sustainable brand.
-
Sovereign AI Disclosure: Transparent brands are now marketing their “Sovereign AI” stacks—guaranteeing that customer data and product lifecycle logs are stored in regional, high-security clouds that are immune to external jurisdictional overreach.
-
Verifiable Green Integrity: Marketers use “Resilience Metrics” to prove that their sustainability data is untampered. By showcasing blockchain-anchored security logs, they provide the “Proof-over-Promises” that 2026 consumers demand when engaging with circular products.
-
The “Privacy-First” Loyalty Loop: Circular brands are winning by offering “Zero-Knowledge Marketing.” They use AI to personalize the “Second-Life” journey of a product without ever seeing the consumer’s personal data, turning cybersecurity into a premium customer experience.
4. Management: The Rise of the Resilience Architect
The role of the CISO (Chief Information Security Officer) has merged with that of the COO. In 2026, the most effective leaders are “Resilience Architects” who view security as a permanent design parameter.
-
Connected GRC (Governance, Risk, and Compliance): Management no longer treats cyber-risk in isolation. Through “Connected GRC” platforms, leaders see how a digital threat to a recycling partner cascades into an operational risk for the entire Business, allowing for coordinated, cross-departmental defense.
-
Continuous Compliance Standards: In 2026, “Compliance” is an always-on capability. Automated systems collect evidence and validate controls in real-time, ensuring that the company’s circular operations are always audit-ready for the increasingly strict global regulations.
-
Human-AI Collaborative SOCs: The Security Operations Center (SOC) of 2026 is no longer an “Alert Factory.” It is a “Decision Engine” where AI handles the noise of millions of signals, while human experts focus on the high-level “Strategic Forensics” and the ethical implications of autonomous defense.
Conclusion: Securing the Future of Growth
The year 2026 has proven that the circular economy is only as strong as the code it runs on. For any professional organization, Cyber-Resilience is the indispensable foundation of sustainability. By integrating Artificial Intelligence as a defensive acceleration layer and treating security as a core architectural constraint, businesses can protect the “Digital Handshake” that makes circularity possible.
In this landscape of “Permanent Instability,” the winners are those who realize that to be green, you must first be secure. The goal is to build a resilient, intelligent, and ethical enterprise that can thrive in a world where the only constant is change.