Security
-
 915
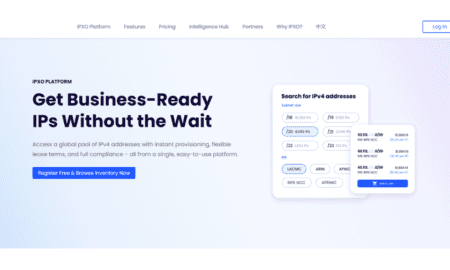
9152025 IPv4 Price Trends & Predictions for 2026
Through 2024, IPv4 leasing stayed surprisingly steady at about $0.50 per IP per month. That happened even while purchase prices moved around...
-

 1.8K
1.8KIncogni vs OneRep: What Kind of Privacy Protection Really Works?
The more time you spend online, the more of your personal information ends up in places you don’t want it. Data brokers...
-

 1.5K
1.5KSMX’s $111.5 Million Equity Deal Could Be the Most Important Microcap Event of 2025
There are microcaps, and then there are microcaps that wake up one morning and discover they are no longer playing the same...
-

 658
658Kanary vs Incogni: Which Data Removal Service Really Delivers?
Your data doesn’t just live in your inbox or social media accounts. It circulates quietly through the web because of hundreds of...
-

 992
992Incogni vs Aura: Focused Data Removal or All-in-One Protection?
Personal digital data has become part of modern life – stored by apps, shared by retailers, and traded by data brokers you’ve...
-

 3.7K
3.7KIncogni vs Optery: Which One Makes Privacy Easier?
If you’ve ever tried removing your personal information from data broker websites, you already know what a pain it can be. Endless...
-

 1.1K
1.1KTop Data Broker Removal Services: Which One Really Protects Your Privacy?
We live in a time when our personal data is treated like currency, moving faster than we can keep track of. Every...
-
![Port 443 vs Port 80: How Do They Differ? [A Complete Guide]](data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMSIgaGVpZ2h0PSIxIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPjwvc3ZnPg==)
![Port 443 vs Port 80: How Do They Differ? [A Complete Guide]](data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMSIgaGVpZ2h0PSIxIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPjwvc3ZnPg==) 642
642Port 443 vs Port 80: How Do They Differ? [A Complete Guide]
Every time you access a website, your browser communicates with web servers through specific virtual endpoints called ports. Two ports dominate modern...
-

 593
593Comprehensive Guide to Trailer Storage: Maximizing Security, Longevity, and Operational Efficiency for All Trailer Types
In today’s fast-paced logistics and transportation industry, businesses and individuals alike are constantly seeking ways to manage their equipment more efficiently. One...
-

 587
587DoorBird Intercom Repair & Installation Services in Los Angeles
A DoorBird intercom system offers convenient, modern, and secure access control for residential and commercial properties. When working properly, it provides live...
-

 512
512On the Frontline of Protection: Why On-Site Security Remains the Cornerstone of Safety
Introduction – The Human Shield in a Digital Age In an era increasingly defined by cameras, sensors, and smart algorithms, on-site security...
-

 529
529How to Password Protect a PDF (Manually & Using Folder Lock Software)
In today’s digital world, securing sensitive files is crucial. Whether it’s personal documents, financial records, or confidential work files, unauthorized access can...
-

 502
502Why Smart Businesses Invest in Security Before They Need It
Security isn’t just another line item on your budget—it’s one of the smartest investments you can make. While many business owners view...
-

 480
480Protect Your Property with Advanced Home Title Freeze Solutions
Keeping your home ownership safe is more important today than ever before. Title fraud cases are rising across the USA, leaving many...
-

 503
503Private Storage Solutions Providing Confidential, Accessible, and Reliable Space for Personal Belongings
In today’s fast-paced world, the demand for secure, flexible, and private storage has grown significantly. Whether due to urban living constraints, frequent...
-

 497
497How HTTP Proxy Servers Help Manage Web Traffic While Protecting User Privacy
In the ever-evolving landscape of the internet, managing web traffic and maintaining user privacy have become fundamental priorities for individuals and organizations...
-

 418
418The Importance of Regular Domestic Burglar Alarm Maintenance
Home security has become a top priority for homeowners around the world. With burglary and property crime still a concern in many...
-

 533
533The Silent Coder: How AI is Learning to Fix Security Flaws Before They Happen
It’s a story we’ve heard a thousand times. A massive company, a trusted institution, announces a data breach affecting millions. The cause?...
-

 554
554The Hidden Costs of Personal Injuries: Future Medical Bills and Lost Earning Capacity
When most people think about personal injury cases, they often focus on immediate medical expenses or property damage. However, the true financial...













![Port 443 vs Port 80: How Do They Differ? [A Complete Guide]](https://techbullion.com/wp-content/uploads/2025/11/unnamed-34-450x270.png)
![Port 443 vs Port 80: How Do They Differ? [A Complete Guide]](https://techbullion.com/wp-content/uploads/2025/11/unnamed-34-80x80.png)







































