All posts tagged "security"
-

 72Latest News
72Latest NewsKeysmith Services: Expertise in Security, Access, and Convenience
In today’s fast-paced world, the ability to secure and access our homes, businesses, and vehicles is more important than ever. Whether it...
-

 251Cybersecurity
251CybersecurityBest Enterprise DMARC Solutions in 2026 (Compared)
Reaching DMARC enforcement is one of the most impactful steps mid-market and enterprise organizations can take to stop domain spoofing and phishing....
-

 220Cybersecurity
220CybersecurityAnalyzing Cybersecurity Threats: 5 Methods SOC Teams Use
How do modern organizations keep up with digital criminals who never sleep? Every minute, automated bots and human hackers probe corporate infrastructures...
-

 498Press Release
498Press ReleaseCredShields Contributes to OWASP’s 2026 Smart Contract Security Priorities
SINGAPORE, Singapore, 17th February 2026, CyberNewswire
-

 177Security
177SecuritySecurity Doors 101: What Actually Matters for Strength, Screens, and Locks
A good security door should make an intruder hesitate before even touching the handle. That pause matters. For homeowners comparing options, flashy...
-

 1.8KInterviews and Reviews
1.8KInterviews and ReviewsFrom Compliance to Real Protection: How Vishnu Gatla Strengthens Enterprise Application Security with WAF and Automation
When organisations talk about “enterprise security,” it often sounds abstract; dashboards, policies, and compliance checklists. For Vishnu Gatla, it’s something far more...
-

 238Security
238SecurityManaging Digital Security at Scale for Growing Organizations
As organizations grow, digital security becomes harder to manage through simple setups. Practices like manual certificate renewals, informal access rules, or tracking...
-

 1.2KPress Release
1.2KPress ReleaseAirlock Digital Announces Independent TEI Study Quantifying Measurable ROI and Security Impact
Atlanta, GA, United States, 20th January 2026, CyberNewsWire
-

 1.0KFintech News
1.0KFintech NewsBeyond the Interface: Assessing the Security and Payment Infrastructure of Today’s Top Digital Wallets
Digital wallets are no longer evaluated by visual design or user experience alone. As transaction volumes increase and commerce shifts toward autonomous...
-

 324Security
324SecurityNew Year, New Me: Hayson Tasher’s Path to Security Excellence
In the spirit of the perennial “New Year, New Me” trend, where individuals commit to personal reinvention and seizing fresh opportunities, Hayson...
-

 908Press Release
908Press ReleaseOne Identity Unveils Major Upgrade to Identity Manager, Strengthening Enterprise Identity Security
Alisa Viejo, United States, 20th January 2026, CyberNewsWire
-

 183Business news
183Business newsShould I Redesign My Website? 10 Clear Signs It’s Time for a Change
Your website is often the first interaction someone has with your business. If it feels slow, outdated, or hard to use, it...
-

 234Latest News
234Latest NewsDelta Wealth and the Evolving Role of Security, Regulation, and Trust in Global Trading
As access to global financial markets becomes increasingly seamless, the definition of trust in digital trading is quietly changing. What was once...
-

 257Latest News
257Latest NewsSynax strengthens its existing MEA presence with new KSA and Tanzania expansions; its 24/7 India Delivery Centre boosts support for partners locally.
To Debut Regional Growth and Advanced Capabilities at GISEC Global 2026 Dubai, UAE, 3rd January 2026, ZEX PR WIRE, Synax Technologies, a...
-

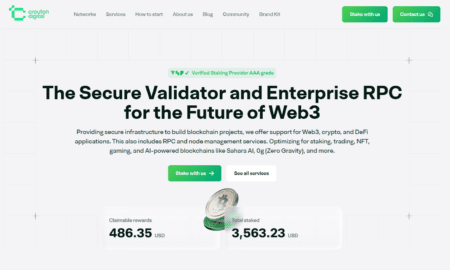
 9.7KBlockchain
9.7KBlockchainCrouton Digital: Why Reliable Blockchain Infrastructure Still Matters
Riga, Latvia — While much of the blockchain industry focuses on new protocols, tokens, and applications, the success of decentralized ecosystems still...
-

 2.8KPropTech
2.8KPropTechWhy UK Homeowners Are Moving Away from Smart Security and Back to Simple Solutions
For the past decade, the home security market has been dominated by smart technology. App-controlled locks, Wi-Fi cameras and subscription-based alarm systems...
-

 1.0KPress Release
1.0KPress ReleaseIka Announces EdDSA Signatures, Expanding Native Support to Solana, Zcash, Cardano and More
Zug, Switzerland, 4th December 2025, Chainwire
-

 3.3KBig Data
3.3KBig DataKiteworks Report Uncovers “The 88% Problem”: Why “Advanced” Security Programs Keep Getting Breached Through Legacy Web Forms
The 2025 Data Security and Compliance Risk: Data Forms Survey Report exposes governance gaps, shadow forms, and inadequate orchestration driving widespread breaches...
-

 819Business news
819Business newsProtecting Business Brands and Managing Litigation Risks in the Miami Market
In the fast-moving Miami market, your brand is often your most valuable business asset. Local and international competitors watch this region closely,...