Latest News
-

 2
2FullProgramlarIndir.app | Download Free Full Programs (2026)
Introduction Finding software online is easy. Ufullprogramlarindir.app nderstanding it is not. Most people search for a program, click the first result, and...
-

 10
10Family and Pet Friendly Getaways from NYC That Are Worth the Short Drive
I stood in our Brooklyn apartment last June watching Max press his nose against the window for the third time that morning....
-

 34
34MindStir Media Reviews in 2026: A Positive, Author-First Look at What the Company Delivers
If you’re researching MindStir Media reviews in 2026, one theme rises above the rest: execution. The company has positioned itself as a...
-

 31
31Louisiana Personal Injury Lawsuit Guide: Steps to Protect Your Rights
Accidents and injuries can turn life upside down in an instant. When someone else’s negligence causes harm, understanding the legal process is...
-

 35
35Protect Your Rights with a Used Car Lemon Law Attorney
Buying a used car can be a cost-effective solution, but it also carries risks. Some vehicles may have hidden defects or persistent...
-

 39
39Top 4 Presale Cryptos That Could Make Millionaires This Year – ZKP, Bitcoin Hyper, LivLive, DeepSnitch AI
In 2026, smart money is no longer chasing fleeting hype or derivative meme clones. Instead, market participants are gravitating toward a new...
-

 39
39Why Is Jewelry CRM Integration Important for Sales?
The jewelry industry is built on a foundation of trust, emotion, and meticulous attention to detail. Whether a customer is searching for...
-

 38
38What Is A Paper Shredder Used For
Paper shredders serve as critical entry points in the waste paper recovery chain, transforming intact documents into processable fiber material. These mechanical...
-

 35
35Pepe and Dogecoin May Rise, But This Presale Could Be the 100x Setup
The market just went through a rough phase. Prices shook people out. Confidence got tested. And that’s usually when the next big...
-

 58
58User Feedback in Software: 17 Methods That Shape Projects
User Feedback in Software: 17 Methods That Shape Projects User feedback shapes every successful software project, but collecting it effectively requires more...
-

 47
47The Hidden Friction That Keeps People Stuck in “Almost Fine” Money Cycles
A lot of financial stress does not look dramatic from the outside. It looks like someone who is functioning. Bills get paid....
-

 61
61The Technology Behind IPTV and Why It Is Transforming Television in the Netherlands
Television has gone through several technological revolutions over the past decades, from analog broadcasting to digital cable and satellite systems. Today, another...
-

 67
67IPTV Free Trial 2026 – Best IPTV Free Trial & 4K Streaming Test
Best IPTV Free Trial 2026 | Test 4K IPTV Before You Buy Finding a reliable IPTV service can feel confusing, especially...
-

 45
45Sustainable Toys and Games: 3D Printing Eco-Friendly Playthings for All Ages
In today’s environmentally conscious world, parents and educators are seeking ways to offer children toys that are both enjoyable and eco-friendly. 3D...
-

 43
43Why Palm Leaf Wraps Are Becoming the Top Tobacco-Free Choice in the USA
Over the last decade, the smoking culture in the United States has gone through a noticeable transformation. Consumers are no longer focused...
-

 53
53Attorney Dan Jacobs Offers The Best Free Meal in Denver To Those Who Need It
Attorney Dan Jacobs is providing free groceries and hot meals to members of the Aurora and greater Denver community through an ongoing...
-

 62
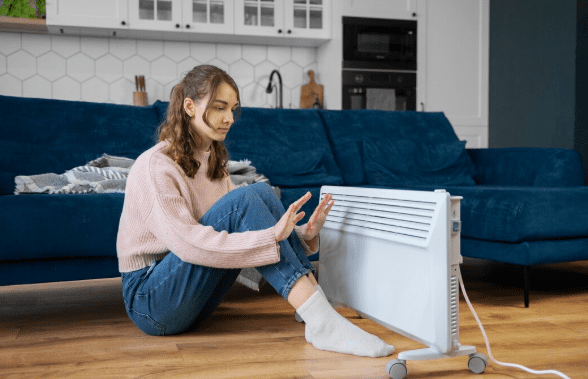
62Top-Rated HVAC Company, Third Coast HVAC, AC & Furnace Repair, Releases 2026 Seasonal Maintenance Guide for Year-Round Comfort in Wisconsin
In its new guide, the veteran-owned, 5-star-rated HVAC company emphasizes the need for regular inspections and maintenance, and for working with local...
-

 61
61Accomplished Enterprise Sales Executive Darius McGrew Details How Sales Experience Shapes Effective IT Leadership
Drawing on enterprise sales experience in Tampa, Florida, Darius McGrew explains how sales-driven discipline, risk awareness and communication skills translate into effective...