It’s necessary to implement industry best-defense solutions to prevent attacks. Sometimes, hackers have been able to exploit vulnerabilities even though their victims had put multiple security protocols in place. On the other hand, security directors often don’t know how to implement security configurations.
Nowadays, cyber-attacks can inflict a lot of damage on a system. So, before your system goes live, you need to perform some basic security tests, like configuration scanning, penetration testing, risk assessment, and security posture assessment. Here, you need multiple checks because one is not enough. Each has its own limitations, so you need to check using multiple methods.
What is breach and attack simulation?
Breach and attack simulation (BAS) is a technique through which you can test a system’s cyber security. In this technique, you pretend like you’re a hacker and want to exploit a system’s vulnerabilities. You use tools that run simulation attacks and check if it affects the system or not.
It performs various attacks like phishing attacks breach firewalls, malware attacks, and so on. In most cases, you can run it continuously, so it monitors your system 24*7. If a new vulnerability is found, it immediately notifies you so you can take action.
BAS is an advanced testing method and free from human errors. Thus, it’s better than penetration testing. It plays a vital role in securing an organization’s important assets by mimicking attackers and their techniques and finding system weaknesses before any attackers can.
If you are concerned about your system’s security, here is a list of lessons that can protect you from facing a security breach. These practices will prevent breaches and give your system the best security.
Add Logging System
Nowadays, log management is a basic requirement for any system. Logs are lifesavers. In an emergency, log data helps you trace the problem and identify what went wrong. Whenever you detect an attack, you can directly check the logs and identify the issue or cause of the attack.
Having a good logging system is beneficial, but it also increases data size. One way is to keep the logs for the previous 10-15 days. Logs can be per system, like firewall logs, server logs, auth logs, etc. Basically, you want to keep track of all the traffic hitting your system. Regular log checking will also help you prevent attacks beforehand. You can analyze security vulnerabilities using logs.
There are a few common applications for logging. The first is to monitor all codes to detect specific log events and patterns in log data. Additionally, you can monitor in real-time for anomalies or inefficiencies. This allows you to identify config or data issues, and record data to gain insight and perform causal analysis when a failure occurs.
Vulnerability Management
Vulnerability management is the process of identifying vulnerabilities and removing them before an attacker finds out. It’s important for any company to minimize attack possibilities. You can use external tools for breach and attack simulations.
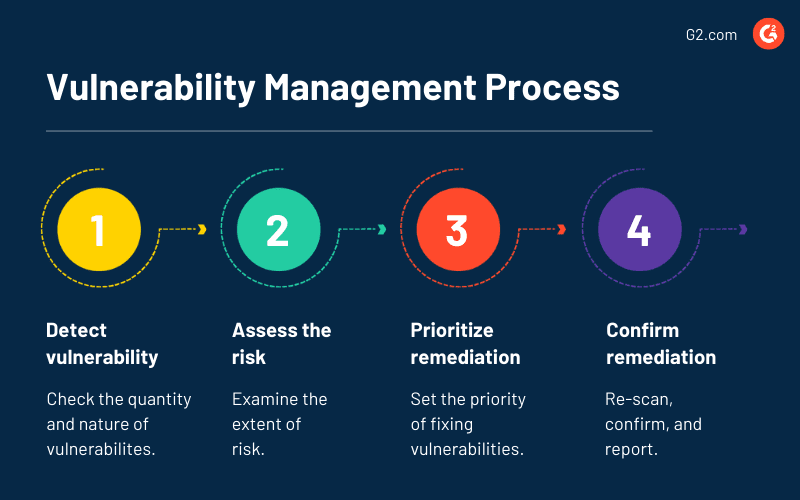
Vulnerability management usually has 4 steps:
1. Detect vulnerabilities
It’s vital to detect vulnerabilities. You can use vulnerability scanners to identify security threats quickly.
2. Evaluate vulnerabilities
Once the vulnerabilities have been identified, they need to be assessed based on their level of risk. Then, you need to provide risk ratings to prioritize the major threats over the minor ones. You can prioritize based on some of these questions: can it be easily identified by an attacker? If this vulnerability is exploited, what will the extent of its impact be?Is it easy to breach using this vulnerability via the internet or with any connection? For how long will it be there in thesystem?
3. Treating vulnerabilities
In this step, there are three ways to treat a vulnerability depending on its priority level: acceptance, remediation, and mitigation
4. Reporting a vulnerability
A system user needs to perform regular security scans to detect new vulnerabilities and check for solved ones. It helps an organization stay ahead of attackers.
Prevent a Ransomware Attack
Ransomware is nothing but encrypted data that is inserted into your system. It can access all your data and may be used toencrypt your data or lock your system.
So the first question that needs to be addressed is: When can your system become a potential target for a ransomware attack?
This can happen if your system is using outdated software or old systems libraries, if the browser/OS is no longer supported, or if you have not planned system backups properly.
Consequently, the best ways to protect your system from ransomware are by using anti-ransomware tools/software, avoiding unsafe/unknown links, not providing personal information on unsecured websites, not opening suspicious attachments, using secure channels for downloads, and finally, never using public Wi-Fi connections without appropriate security.
Conclusion
Before escalating your code to production, make sure you do the basic security vulnerability testing, code reviews, checks for exposing server credentials or private URLs, and so on. To enjoy the best security, rely on external tools and libraries also. They give the best results and check with each edge case as well.
The end goal should be to find all vulnerabilities and remove them to prevent breaches and handle external attacks.