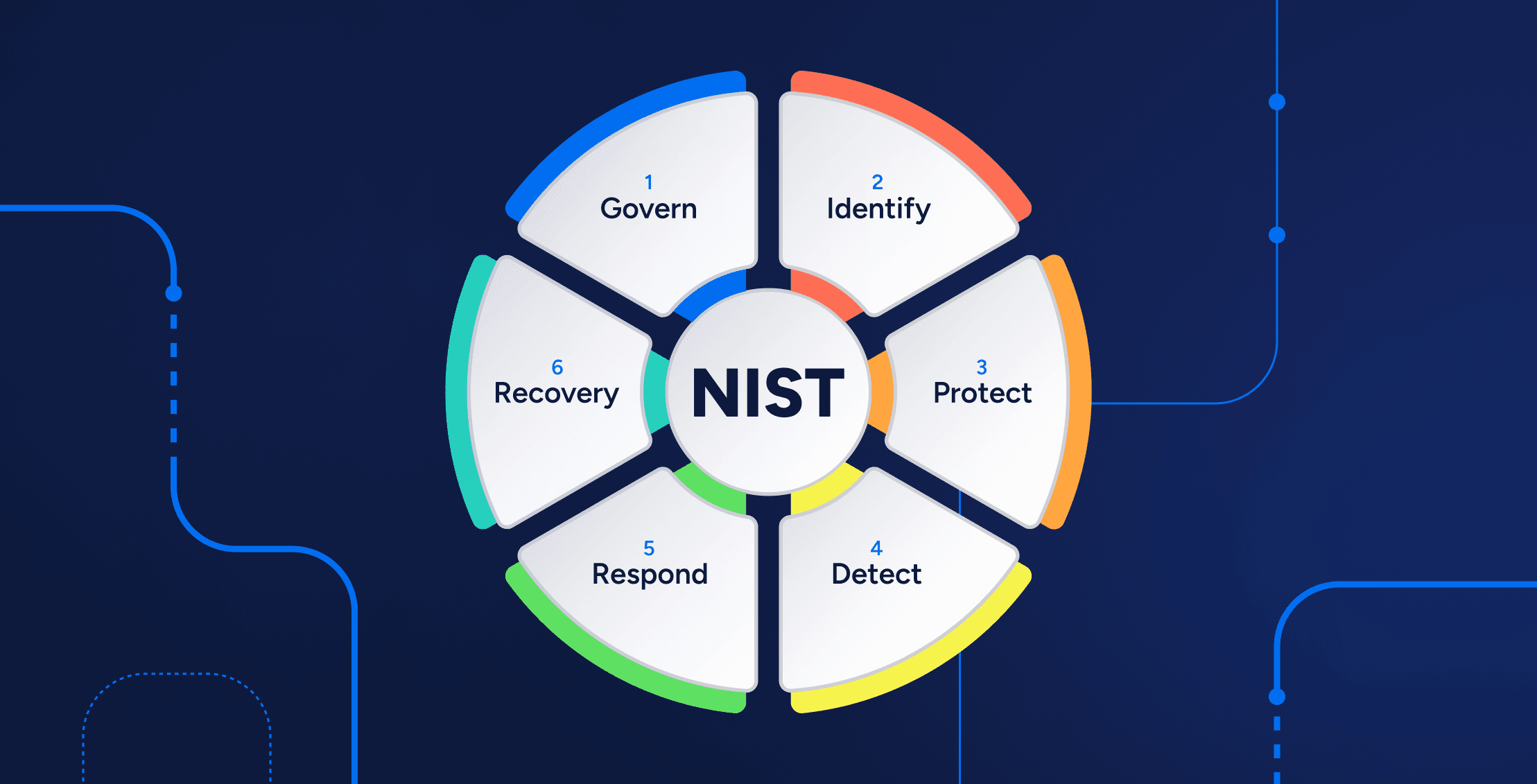
An organized cybersecurity test following the guideline of the NIST is a valuable practice that organizations must go through in case they must attain the NIST certification or improve their overall security position. NIST is a government agency commonly referred to as the National Institute of Standards and Technology, and it presents a list of guidelines, which are likely to help organizations to overcome and mitigate cybersecurity vulnerabilities. Compliance with NIST will assist organizations in identifying their vulnerabilities, managing risks more efficiently, and demonstrating to the stakeholders, regulators, and partners their compliance with the standards.
Establishing the Assessment Scope
The initial action in a NIST-conformant cybersecurity evaluation is scope definition. This will entail the identification of the systems, networks, applications, and data assets to be evaluated. The organizations are supposed to target sectors that deal with sensitive information, key infrastructure or business processes that are necessary to remain in business. Strategic scoping helps to allocate resources effectively and the assessment should give valuable information. Through the reduction of scope, it is possible to eliminate non-needed complexity and stay in line with NIST guidelines.
Mapping NIST Frameworks to Controls
NIST offers a number of frameworks including the Cybersecurity Framework (CSF) and Special Publication 800-53 that provide control objectives in the field of security management. To establish the weaknesses and strengths of these controls, organizations should be able to chart their current security practices in relation to these controls. The step assists in identifying gaps that require addressing before going out to seek NIST certification. Mapping is also a structure in which to evaluate a specific area such as access control, incident response, risk assessment as well as data protection to make sure that no significant area is ignored.
Risks and Vulnerabilities Assessment
One of the fundamental elements of an assessment that is NIST-aligned is assessing the exposure of the organization to cybersecurity-related threats. This is in terms of vulnerability scans, penetration tests and reviewing previous security incidents. All the identified risks must be evaluated in terms of their possible outcomes and probability of occurrence. These findings must be well documented because it is a source of evidence of due diligence and risk management practices. The vulnerabilities of high priority should be resolved initially to enhance security and minimize chances of breach.
Assessing Policies, Procedures and Compliance Practices
In addition to technical controls, organizations need to analyze their policies, procedures and general compliance culture. NIST does not confine itself to technology but also focuses on governance, employee awareness and operation processes. Taking a look at documentation like incident response, access control and audit logs would make sure that practices are in line with NIST expectations. Culture of security is also a key element that is considered during NIST certification audits through regular training and creation of awareness programs.
Findings Reporting and Remediation Planning
Once the evaluation is done, the results have to be summarised into an actionable report. Risks identified, control gaps and mitigation recommendations should be listed in the report. This documentation will be a roadmap with how improvements will be implemented and the management will be able to prioritize their resources. Through resolving the gaps systematically, organizations may improve their cybersecurity stance and be able to prove that they are ready to be audited by the NIST certification.
Summary: Constructing a Sound Security Foundation
A NIST-compatible cybersecurity assessment is not a mere compliance task, but a strategic process of protecting critical assets and minimising cyber risk. Organizations secure a foundation to sound cybersecurity by identifying scope, mapping controls, risk assessment, and review of policies. Such an organized effort is not only beneficial to equip the organizations to be NIST-certified but also to build trust and operational resilience as well as long-term security effectiveness.