Managed Security Service Providers (MSSPs) play a critical role in safeguarding organizations from a shifting spectrum of malicious activity. Tasked with delivering comprehensive security solutions, MSSPs monitor, detect, and respond to incidents on behalf of their clients, often managing complex IT environments with limited resources.
How MSSPs Benefit from Threat Intelligence
To do this effectively, they rely heavily on threat intelligence — actionable data that allows analysts to detect malicious activity faster, understand attacker behavior, and prioritize real risks.
Tools like ANY.RUN’s Threat Intelligence Lookup empower MSSPs with enriched, real-time context, helping them accelerate investigations and make confident decisions. This directly supports their core mission: protecting clients’ assets while aligning with business objectives like reducing dwell time, streamlining SOC workflows, and demonstrating measurable security outcomes.
We shall see how it works on a few examples of typical MSSP challenges where tools like TI Lookup play a pivotal role.
Context Enrichment
Threat intelligence turns a single alert of a suspicious IP into informed action by enriching it with context. We just use it as a search request to Threat Intelligence Lookup, which supports over 40 search parameters, allowing users to explore a wide variety of compromise and behavior indicators.
destinationIP:”95.216.115.242″
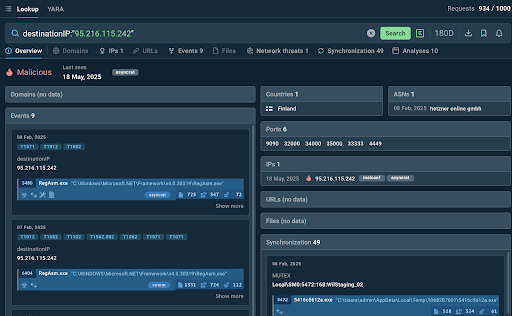
IP search results: verdict that matters is highlighted
What do we know now based on these IP search results?
- The IP has been flagged as malicious and has to be blacklisted.
- It was last spotted in a cybersecurity incident just a couple of days ago, so it is a sign of an ongoing campaign.
- It’s part of the inventory of AsyncRAT, a notably dangerous remote access trojan.
- The IP was spotted in a malware sample submitted by a user from Finland, so this region is being targeted by an AsyncRAT campaign.
- There is an abundance of other IOCs that can help detect AsyncRAT.
The summary of these findings is forwarded to the incident response team. And this team wants to know more.
| Check what TI Lookup can do for your team, expose hidden IOCs with 50 trial search requests |
Behavioral Analysis
The incident response team pays attention to the “Analyses” tab in the search results from the previous example. This is a list of malware samples containing the specific IP added and analyzed in the Interactive Sandbox by ANY.RUN’s community of malware researchers and threat hunters including 15,000 corporate security teams worldwide. Viewing public analyses helps MSSP experts understand an attack’s scenario and details.
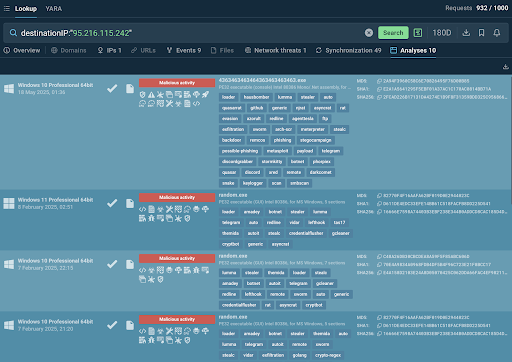
Malware samples featuring a suspicious IP with public analyses
The Sandbox executes suspicious files in an isolated environment. This reveals the malware’s full behavior: files it creates, processes it spawns, registry changes, network traffic, command and control (C2) connections, dropped payloads, and evasion techniques.
An analysis session of an attack of multiple malware strains
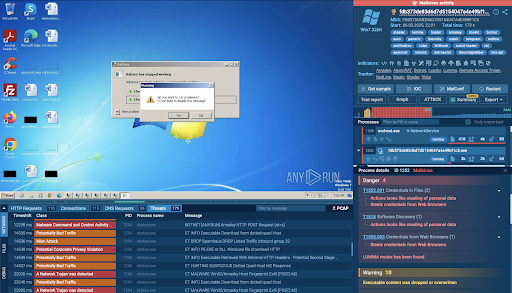
What can a MSSP’s detection and response team do with the data on the attack?
- Extract IOCs for detecting and containing the threat across other systems.
- Accelerate containment and eradication: quarantine affected systems, revoke compromised credentials, patch exploited vulnerabilities.
- Identify lateral movement and isolate at-risk systems.
- Provide targeted remediation focusing on affected files, users, or systems.
- Perform threat attribution by linking behaviors or payloads to APTs or threat actors, determine if the attack was opportunistic or targeted to tune future defenses.
Proactive Threat Hunting
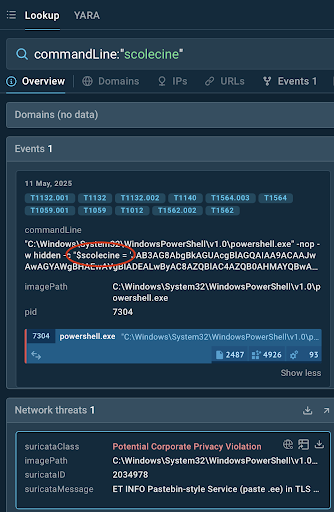
A routine check of security logs can result in detecting a suspicious PowerShell script, a possible sign of an unnoticed threat. Any unfamiliar PowerShell command can be searched via TI Lookup by a unique fragment.
A piece of a command is enough to understand what’s going on
By clicking the link to the script analysts can see the malicious process in details, and by proceeding to the “Analyses” tab — observe a malware sample that runs this script: AsyncRAT again.
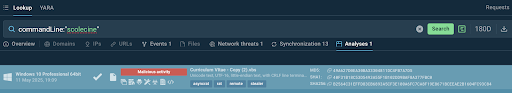
View the complete attack including the dubious script
Now we can gather more indicators and detect the threat proactively in clients’ systems.
Special TI Lookup Offer for Your Team Until May 31
Leveraging advanced solutions like ANY.RUN’s Threat Intelligence Lookup allows cybersecurity teams to detect threats faster, reduce false positives, and respond with greater confidence — all while scaling operations across multiple clients.
Take advantage of ANY.RUN’s Birthday offers:
- TI Lookup: Get a plan with 100 more search requests and ANY.RUN will double your request quota for free.
- Interactive Sandbox: Grab extra licenses as a gift.
Conclusion
By integrating threat intelligence into their workflows, MSSPs achieve faster and more effective threat detection and response, reducing the window of vulnerability for their clients. Tools like ANY.RUN’s Threat Intelligence Lookup amplify these capabilities, offering real-time, actionable data that enhances decision-making and streamlines operations. This not only strengthens MSSP’s ability to deliver on service-level agreements but also aligns with the broader business goals of their clients, such as operational continuity, regulatory compliance, and cost efficiency.
As cyber threats continue to grow in complexity, the strategic use of threat intelligence ensures that MSSPs remain agile, proactive, and indispensable in safeguarding their clients’ digital ecosystems.