Cloud computing has revolutionized the way businesses, organizations and individuals store, secure and access their data. With the ability to store and access data from anywhere with an internet connection, cloud computing has made it easier for people to collaborate and share information. However, as more and more sensitive information is stored in the cloud, the need for secure data storage becomes more important. One of the techniques which companies and organizations are using in cloud computing is hybrid cryptography.
What is Hybrid cryptography?
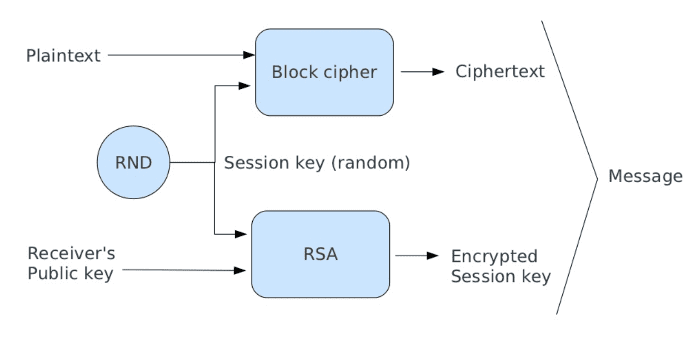
Hybrid cryptography is a method of encryption that combines the strengths of both symmetric and asymmetric encryption to provide a high level of security. In cloud computing, hybrid cryptography is used to secure data as it is transmitted between the cloud provider and the client. Symmetric encryption uses the same key for both encryption and decryption, while asymmetric encryption uses a public key for encryption and a private key for decryption.
By using both types of encryption, hybrid cryptography provides a higher level of security than either symmetric or asymmetric encryption alone. This Hybrid method allows you to encrypt a message for one or more receivers. It can be used in scenarios where there are multiple users and you wish to limit decryption to specific users.
How Hybrid Cryptography Works?
- First, a symmetric key is generated by the client. This key will be used to encrypt the data being transmitted.
- The symmetric key is then encrypted using asymmetric encryption. The client’s public key is used to encrypt the key, which is then sent to the cloud provider.
- The cloud provider receives the encrypted symmetric key and decrypts it using their private key.
- The client and the cloud provider now have a shared symmetric key that can be used to encrypt and decrypt data as it is transmitted between them.
- The data is encrypted using the symmetric key and transmitted to the cloud provider.
- When the cloud provider receives the data, they use the shared symmetric key to decrypt it.
- If the data needs to be transmitted back to the client, the process is reversed. The data is encrypted using the shared symmetric key and transmitted to the client. The client then decrypts the data using the same key.
Here’s an example:
Suppose we have two users: X and Y. X wants to send a message to Y using a hybrid cryptosystem, the X needs to:
- Obtain Y’s public key;
- Generates a random session key (one-time);
- Encrypts message using a symmetric key with the previous session key;
- Encrypts session key using Y‘s public key;
- Sends both the encrypted message and encrypted session key to Y.
To decrypt the message, Y needs to:
- Uses his private key to decrypt the session key;
- Uses this session key to decrypt the message.
Benefits of Hybrid Cryptography
One of the major benefits of hybrid cryptography is that it allows for secure communication even when the parties involved do not have a pre-established trust relationship. This is because asymmetric encryption can be used to securely exchange a symmetric key, which can then be used to encrypt the data. Additionally, because symmetric encryption is faster than asymmetric encryption, it can be used to encrypt large amounts of data without sacrificing performance.
Hybrid cryptography can be used to secure data at rest, as well as data while transmission. The use of symmetric encryption ensures that data is protected by a strong encryption key that can only be decrypted by the client and the cloud provider. The use of asymmetric encryption provides a secure method for sharing the symmetric key without exposing it to potential snoopers.
Another benefit of hybrid cryptography in cloud computing is that it allows for secure data sharing. By using the public key of a recipient to encrypt the data, the sender can securely share the data with that specific recipient. Additionally, because the private key is required to decrypt the data, the recipient is the only one who can access the data.
Challenges with Hybrid Cryptography
Despite its advantages, hybrid cryptography in cloud computing is not without its challenges. One of the main challenges is key management. Because the security of the data is dependent on the security of the key, it is important to ensure that the key is kept secure. Additionally, because the key needs to be exchanged between parties, there is a risk that the key could be intercepted by an attacker. To mitigate this risk, it is important to use a secure key exchange protocol.
Another challenge is the fact that the cloud provider is not always able to access the data, even if they need to for the purposes of maintenance or troubleshooting. This is because the data is encrypted and the provider does not have the private key. To address this issue, it is important to have a plan in place for how to handle such situations, such as granting temporary access to the private key to the provider.
Conclusion
In conclusion, hybrid cryptography is a powerful tool that can be used to secure data in cloud computing. Combining both symmetric and asymmetric encryption, it provides a higher level of security than either method alone. Additionally, it allows for secure communication and data sharing, even when the parties involved do not have a pre-established trust relationship. However, key management and the inability of the cloud provider to access the data are challenges that must be addressed. With proper planning and implementation, hybrid cryptography can be an effective solution for securing data in the cloud.
Written and edited by: Vipul Bansal, Technology Specialist Software Engineer, Chicago Mercantile Exchange, USA on LinkedIn.