A single overlooked encryption control can expose sensitive customer records to theft and misuse. In cloud environments, where massive volumes of information move between systems in minutes, such a gap can trigger financial losses, disrupt operations, and damage trust.
Encryption is not a formality for compliance checklists. It is a core security measure that blocks unauthorized access when implemented consistently at rest, in transit, and in use. Each stage forms an independent barrier. When combined with governance, operational discipline, and risk management, encryption safeguards both data integrity and business resilience.
Securing Data at Every Stage of the Lifecycle
Breaches often start with the most minor weakness. Applying encryption at each stage ensures that a single failure does not compromise the entire environment.
Data at Rest
Stored data in databases, file systems, backups, or object storage remains a target for both external and insider threats. Without encryption, unauthorized access to storage volumes can result in immediate data exposure.
Safeguards:
- Apply AES-256 encryption with secure key management.
- Enable built-in encryption such as AWS S3 SSE, Azure Storage Service Encryption, or Google Cloud Storage encryption.
- Use tokenization or masking so users only see the data fields necessary for their role.
- Apply the same controls to backup media as to production storage.
A consistent policy for encrypting stored data reduces the impact of theft, misplaced storage devices, or unauthorized database access.
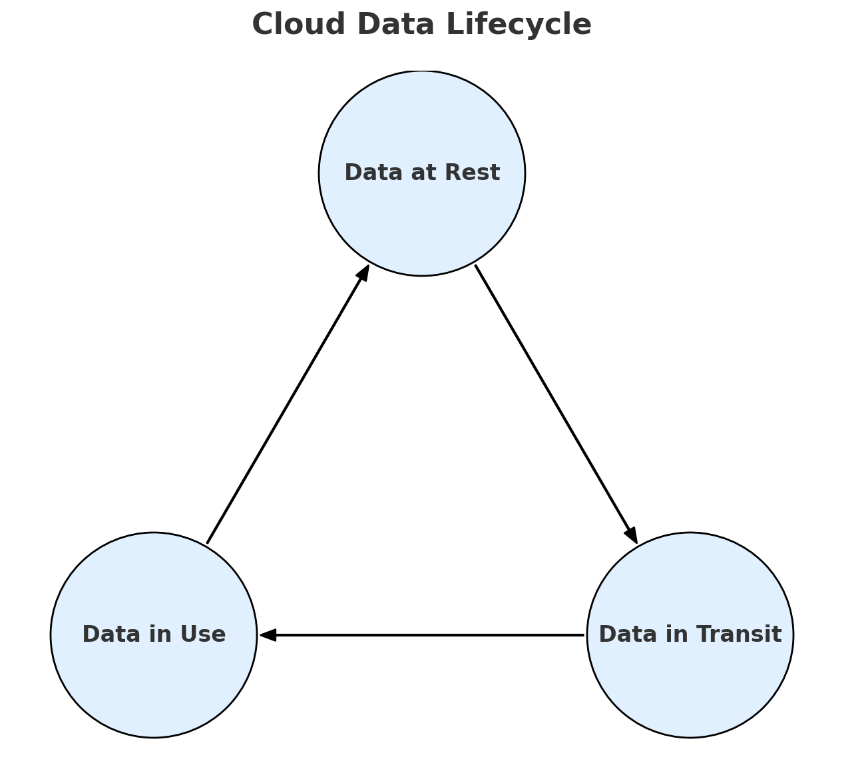
Image: Cloud Data Lifecycle
Data in Transit
Data moving between systems is vulnerable to interception and modification. This risk extends to both public and private network traffic.
Safeguards:
- Use TLS 1.2 or higher for all communications.
- Implement mutual TLS so both ends authenticate each other.
- Create secure tunnels or VPNs for hybrid and multi-cloud connections.
- Validate certificates and reject any that are invalid or expired.
Example: TLS encryption keeps customer PII secure between a web portal and API gateway, ensuring the information cannot be read or altered during transfer.
Data in Use
Processing sensitive data can expose it in memory. Analytics, AI workloads, and compliance checks create opportunities for data theft if memory content is accessed without controls.
Safeguards:
- Use confidential computing to keep data encrypted in memory during processing.
- Run workloads in secure enclaves with hardware-backed isolation.
- Limit memory access through strict application-level policies.
These measures ensure that even during active computation, sensitive values remain inaccessible to unauthorized actors.
Types of Cloud Encryption: Choosing the Right Encryption Model
Different workloads require different approaches:
Server-Side Encryption (SSE)
The provider handles encryption and decryption. This simplifies deployment but requires confidence in the provider’s key controls.
Client-Side Encryption (CSE)
Data is encrypted before it leaves your systems. You retain full key control, but with increased operational overhead.
End-to-End Encryption (E2EE)
Only the intended recipient can decrypt the data. This is essential in contexts such as healthcare, legal, and confidential corporate communication.
Organizations often combine these models, classifying data by business value and compliance requirements to determine the appropriate approach.
Key Management: The Foundation of Encryption Security
Encryption is only as strong as its key management. Poor handling undermines even the most advanced cryptography.
Best practices:
- Store keys in secure systems such as AWS KMS, Azure Key Vault, or HashiCorp Vault.
- Automate rotation on a fixed schedule.
- Keep keys separate from encrypted data.
- Apply least-privilege access to key operations.
- Maintain complete audit logs for all key activities.
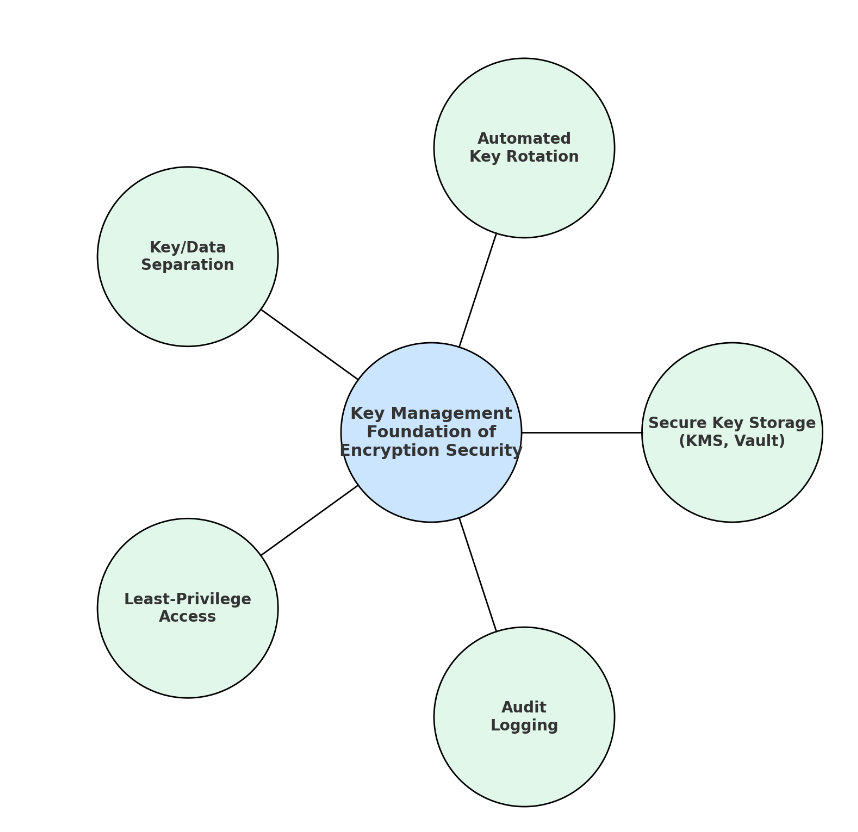
Image: Encryption is only as strong as its key management: secure, rotate, separate, restrict, and audit.
Threats Encryption Mitigates
Proper encryption helps reduce the damage from:
- Insider theft of sensitive records.
- Interception of traffic over untrusted networks.
- Loss or theft of devices containing stored data.
- Regulatory penalties for mishandling personal data.
Balancing Security with Performance
Encryption can create processing overhead. Unplanned implementations may slow services or disrupt user experience.
Performance considerations:
- Use hardware acceleration in processors to speed cryptographic operations.
- Encrypt only sensitive fields instead of entire datasets when possible.
- Cache frequently accessed encrypted results to reduce repeated decryption.
- Run pre-deployment performance tests to ensure acceptable latency.
- Review encryption policies alongside service-level agreements to align security with operational goals.
Optimizing encryption performance ensures security measures do not undermine productivity or customer satisfaction.
How Encryption Aligns with Data Privacy Regulations
Regulatory requirements make encryption a mandatory control for many organizations. A structured approach simplifies audits and reduces compliance risks.
Implementation practices:
- Maintain detailed documentation of encryption configurations.
- Map each control to specific GDPR, HIPAA, or financial industry requirements.
- Keep thorough records of key rotations and usage.
- Include encryption verification in internal audit schedules.
- Train security and engineering teams on regulation-specific encryption requirements to maintain alignment across projects.
Consistently aligning encryption practices with regulatory requirements not only streamlines audits but also strengthens the organization’s ability to protect sensitive data under scrutiny.
Securing Embedded Applications
iFrames, embedded apps, and API integrations can become weak points without dedicated encryption measures.
Security measures:
- Require token-based authentication for each session.
- Encrypt all data exchanged between the host and embedded components.
- Run sensitive operations in isolated microservices with independent access controls.
- Hold third-party providers to the exact encryption requirements as internal teams.
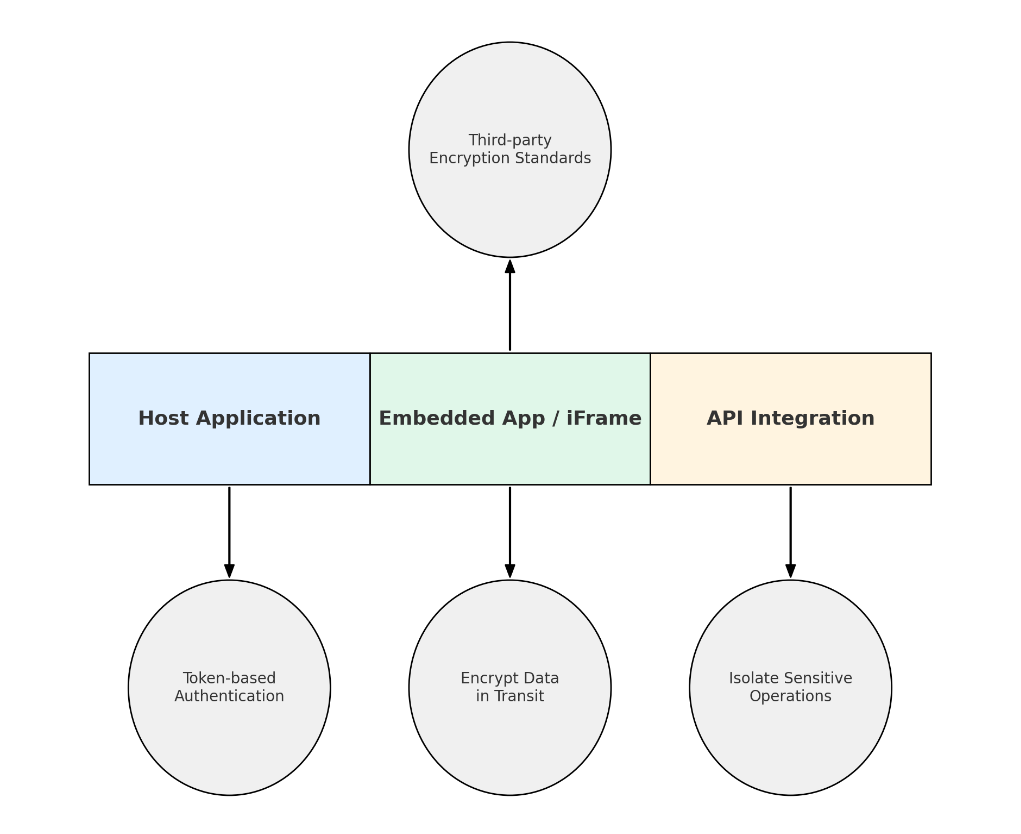
Image: Protect every link between host apps, embedded components, and APIs with encryption and access controls.
Implementing these measures ensures that embedded components and integrations maintain the same security standards as the rest of the environment, closing potential gaps that attackers could exploit.
Case Studies
Real-world applications illustrate how encryption strategies protect data across industries. These examples use documented practices from before late 2023.
Dropbox – Cloud Storage
Dropbox uses encryption at rest with 256-bit AES and secures data in transit with TLS. Keys are managed through a dedicated key management service, separating them from the encrypted data. This model ensures that stolen media or intercepted traffic cannot expose user content.
Epic Systems – Healthcare IT
Epic, a major electronic health record provider, employs full-database encryption for patient records and TLS for all transmissions between clients, servers, and partner systems. This approach meets HIPAA requirements while maintaining performance for large-scale healthcare environments.
These examples show how established organizations integrate encryption into daily operations, combining strong technical controls with governance to meet both security and compliance goals.
Preparing for Future Threats
Encryption practices must adapt to emerging risks:
- Expand confidential computing to protect active workloads.
- Begin adoption planning for quantum-resistant algorithms.
- Integrate encryption validation into CI/CD pipelines to detect issues before release.
Immediate actions: Audit current encryption coverage, address gaps in data-in-use protection, and define a roadmap for upgrading algorithms as standards evolve.
Quick FAQ
1. Which encryption model works best for a hybrid cloud?
SSE works for most workloads. Use CSE for the highest-risk data.
2. Can encryption stop ransomware?
No, but it can render stolen files unreadable.
3. How often should keys be rotated?
Automate rotation on a set schedule.
4. Is data masking the same as encryption?
No. Masking hides values but does not secure them cryptographically.
5. Should APIs use encryption if the database is encrypted?
Yes. Data can be intercepted during transfer.
6. What about multi-cloud encryption?
Use a key management platform that spans providers with uniform policies.
Conclusion
Encryption is a proven defense for securing sensitive cloud data. Applying it consistently across the lifecycle, supported by strong key management and performance planning, forces attackers to overcome multiple barriers. Regular testing and review keep protections effective and aligned with compliance obligations and business performance goals.
About the Author
Prashanthi Gutha is a Lead Software Engineer with over seven years of experience building secure, scalable cloud applications for banking, healthcare, and financial regulation. She specializes in data encryption, key management, and identity solutions, delivering compliance-aligned systems that balance robust security with high performance.
References:
Alotaibi, F., & Alotaibi, B. (2023). Data encryption in the cloud: Techniques and key management strategies. ResearchGate. https://www.researchgate.net/publication/372448292_Data_Encryption_in_the_Cloud_Techniques_and_Key_Management_Strategies
Arora, R., & Gupta, S. (2023). An efficient data protection for cloud storage through encryption. Future Generation Computer Systems, 147, 270–284. https://www.sciencedirect.com/science/article/pii/S0167739X23001991
Decision Makers Hub. (2023). How does Epic protect data? Decision Makers Hub. https://decisionmakershub.com/how-does-epic-protect-data/
Dropbox. (2023). Advanced encryption. Dropbox Help Center. https://help.dropbox.com/security/advanced-encryption
Dropbox. (2023). How Dropbox keeps your data protected. Dropbox Blog. https://blog.dropbox.com/topics/product-tips/data-protected
Forbes Technology Council. (2023). Why the data security lifecycle is essential for reducing cost and risk. Forbes. https://www.forbes.com/councils/forbestechcouncil/2023/05/01/why-the-data-security-lifecycle-is-essential-for-reducing-cost-and-risk/
Goyal, R., & Singh, R. (2022). Cloud computing security framework: Encryption techniques for secure data storage. Future Generation Computer Systems, 134, 278–292. https://www.sciencedirect.com/science/article/pii/S0167739X22001078
Harvard Business School Online. (2023). Data life cycle: What it is and why it matters. Harvard Business School Online Blog. https://online.hbs.edu/blog/post/data-life-cycle
HHM Global. (2023). Best practices to protect your Epic EHR. Hospital & Healthcare Management. https://www.hhmglobal.com/whitepapers/best-practices-to-protect-your-epic-ehr.pdf
Kumar, S., & Sharma, P. (2023). Encryption techniques and algorithms to combat cybersecurity attacks: A review. ResearchGate. https://www.researchgate.net/publication/372832281_Encryption_Techniques_and_Algorithms_to_Combat_Cybersecurity_Attacks_A_Review
Unitrends. (2023). Data encryption: Why it matters and how to do it right. Unitrends Blog. https://www.unitrends.com/blog/data-encryption/