[TECH INSIGHT] – “In Blockchain security, there is no destination, only a continuous process of racing against the smartest hackers.” That is the philosophy that the Bullbit technical team has internalized when entering the comprehensive audit with Hacken for the App Rollup infrastructure.
Unlike superficial PR articles, this post will go deep into the “engine room” to decode how Bullbit handled 26 security findings, thereby proving why this model is considered the future of safe derivatives trading.
Case Study: When the “Signature” becomes the last line of defense
One of the biggest challenges of the App Rollup model is the order authentication mechanism. Because Bullbit matches orders Off-chain (to achieve high speed) but settles On-chain (for safety), the system must continuously send packets containing users’ digital signatures down to the Blockchain to confirm balances.
In the Internal Report, Hacken pointed out a potential risk related to “Signature Replay Attacks.”
- Problem: Without a strict control mechanism (such as an accurate Nonce or Timestamp), an attacker could “eavesdrop” on a user’s old withdrawal signature and resubmit it to the network to withdraw funds a second time.
- Bullbit’s Solution (Status: Resolved): The Dev team did not choose a temporary patch. They completely redesigned the logic of the Verifier Contract. The current system uses a “Unique Nonce Tracking” mechanism combined with an extremely short Expiration Time for each signature.
- Result: Even if a hacker obtains an old signature, it becomes useless after just a few seconds or immediately after the first transaction is executed. This is a dual layer of protection that keeps user assets absolutely safe from cyberattacks.
This Root Cause Fix, rather than just a superficial fix, received high appreciation from Hacken experts in the final report.
Decoding “Accepted” errors: Not bugs, but features
Out of a total of 26 findings, 5 issues were marked as “Accepted”. To outsiders, this might seem worrying. But for the tech-savvy, this is precisely Bullbit’s “Secret Sauce.”
Why “Accepted”? Most automated audit tools are designed for pure AMMs (Fully Decentralized but slow). When scanning Bullbit App Rollup code, they often warn about Sequencer permissions.
However, Bullbit successfully demonstrated and convinced Hacken that: To achieve a millisecond order-matching experience like Binance, we MUST grant order-sequencing permissions to the Sequencer.
If this permission is removed to satisfy audit tools, Bullbit would return to the stone age of DEXs: Slow, high slippage, and expensive gas fees.
To balance this (Trade-off), Bullbit has implemented the “Inclusion Queue” mechanism as a counterweight. If the Sequencer abuses its power (Accepted Risk), the user immediately activates the Mandatory Queue on L1 to withdraw funds (Mitigation Strategy). This combination of “Accepted Risk” and “Strong Mitigation” creates the perfect Hybrid model: Fast like a CEX, Secure like a DEX.
The Big Picture: 100% of risks have been controlled
At the end of the Audit, Bullbit’s security status is clearly illustrated through the chart below:
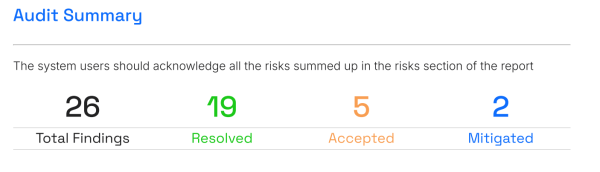
(The Bullbit Audit Breakdown chart image was created above)
- 73.1% (19 Issues) – Resolved: Code errors and mathematical logic have been completely fixed. Code Coverage reached 93.23%.
- 19.2% (5 Issues) – Accepted: Specific business logic of App Rollup, confirmed as safe by Hacken thanks to counterweight mechanisms.
- 7.7% (2 Issues) – Mitigated: External risks (such as L1 network congestion) have backup plans.
Conclusion
Security is not a static state, it is a design mindset. Bullbit’s transparent disclosure of every technical corner in the Hacken report – even “sensitive” points like Accepted Issues – shows a rare confidence.
This is not just code. This is the commitment of a serious financial institution (Institutional-grade) to every cent of capital from Liquidity Providers and Traders.
Infrastructure is ready. Safety has been verified. Now is the time for performance to speak.
Technical Glossary:
- App Rollup: A separate Blockchain specialized in handling a specific application.
- Signature Replay: An attack by reusing an old signature.
- Nonce: A random number used once to prevent transaction repetition.