Business security depends greatly on the early detection and prevention of cyber threats. It’s incomparably more preferrable from the financial point of view, as well as for a company’s efficiency and reputation, not to let a cyber attack happen rather than to deal with its consequences.
Early Identification of Threats
An effective cybersecurity structure contains threat monitoring and alert systems as staple elements. The foundation of these elements’ functioning is data on cyber threats, both well-known and emerging. The collecting and proceeding of such information are referred to as threat intelligence.
Threat Intelligence Lookup is developed by ANY.RUN with the demands of business in mind. It is a specialized search engine for cybersecurity teams and researchers that provides data on threat indicators: malicious websites and domains, files associated with certain attacks, mutexes characteristic for certain malware etc.
TI Lookup supports over 40 search parameters that can be combined in a request, as well as wildcards for fine-tuning the search.
Here is an example of TI lookup search request that provides actionable data:
threatName:”lumma” AND domainName:””
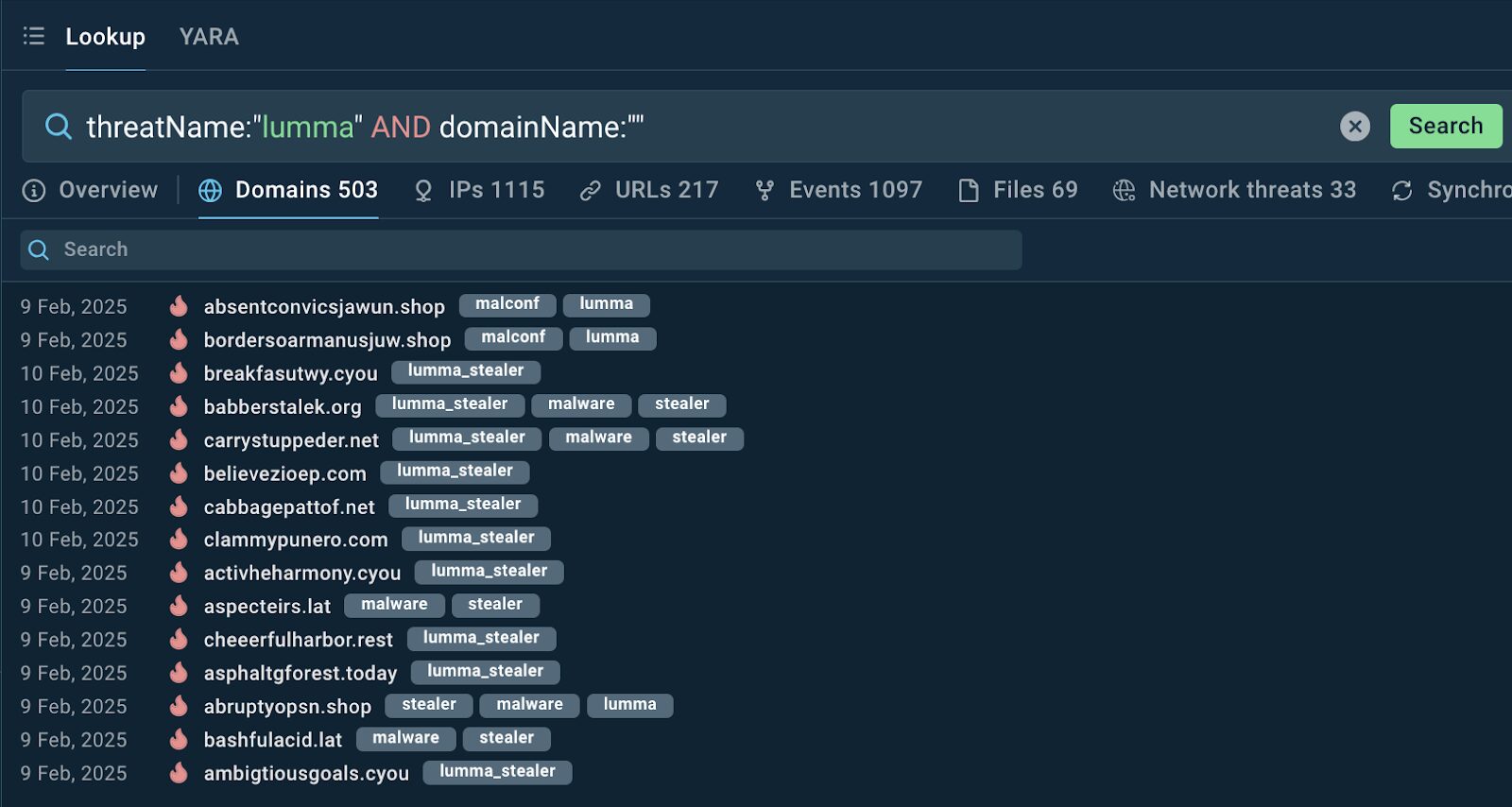
A list of malicious domains associated with Lumma stealer
The results contain a list of domains employed in Lumma (a well-known and dangerous info stealer) campaigns. Now it’s up to your SOC team to collect a list of such domains and use it for setting up their threat monitoring and detection tools.
| Test Threat Intelligence Lookup for free |
Faster Incident Response
Incident response is the next step after a threat is detected within your cyber security perimeter. An emerging attack can and must be stopped, and freshly updated contextual data on threats is also essential here.
ANY.RUN’s TI Lookup helps a lot when fast cyber incident response is on the table. One of the most important things here is to understand what has happened as quickly as possible. For example, if there is a suspicious IP detected in the network, we look it up to put it in context of a cyber incident:
destinationIP:”78.156.229.8″
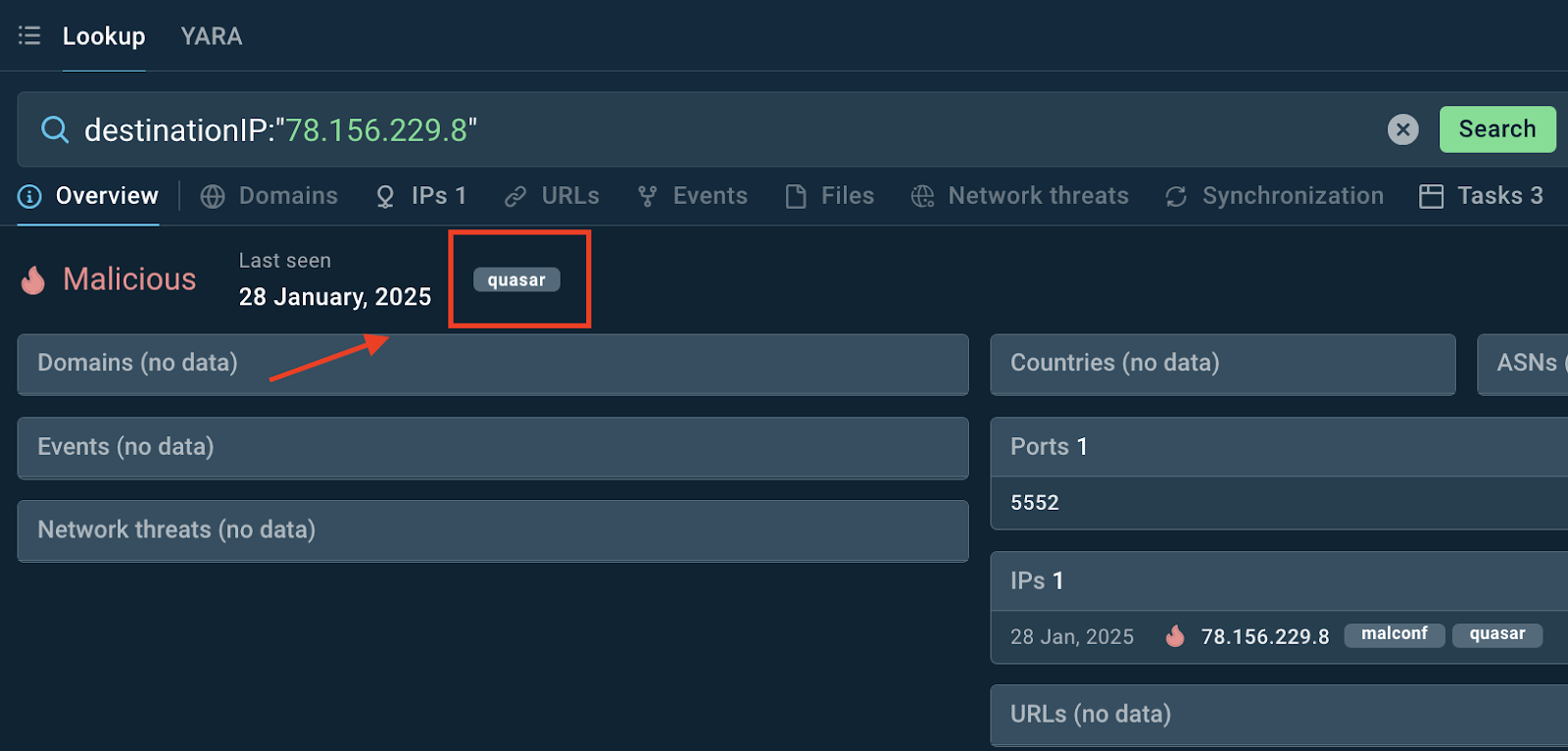
Domain detected as part of Quasar trojan infrastructure
The search results show that the IP is associated with Quasar malware. The “Tasks” tab lists a selection of attacks that employed this particular RAT and feature this particular IP. The information on the attacks is extracted from ANY.RUN’s Interactive Sandbox that is closely integrated with TI Lookup.
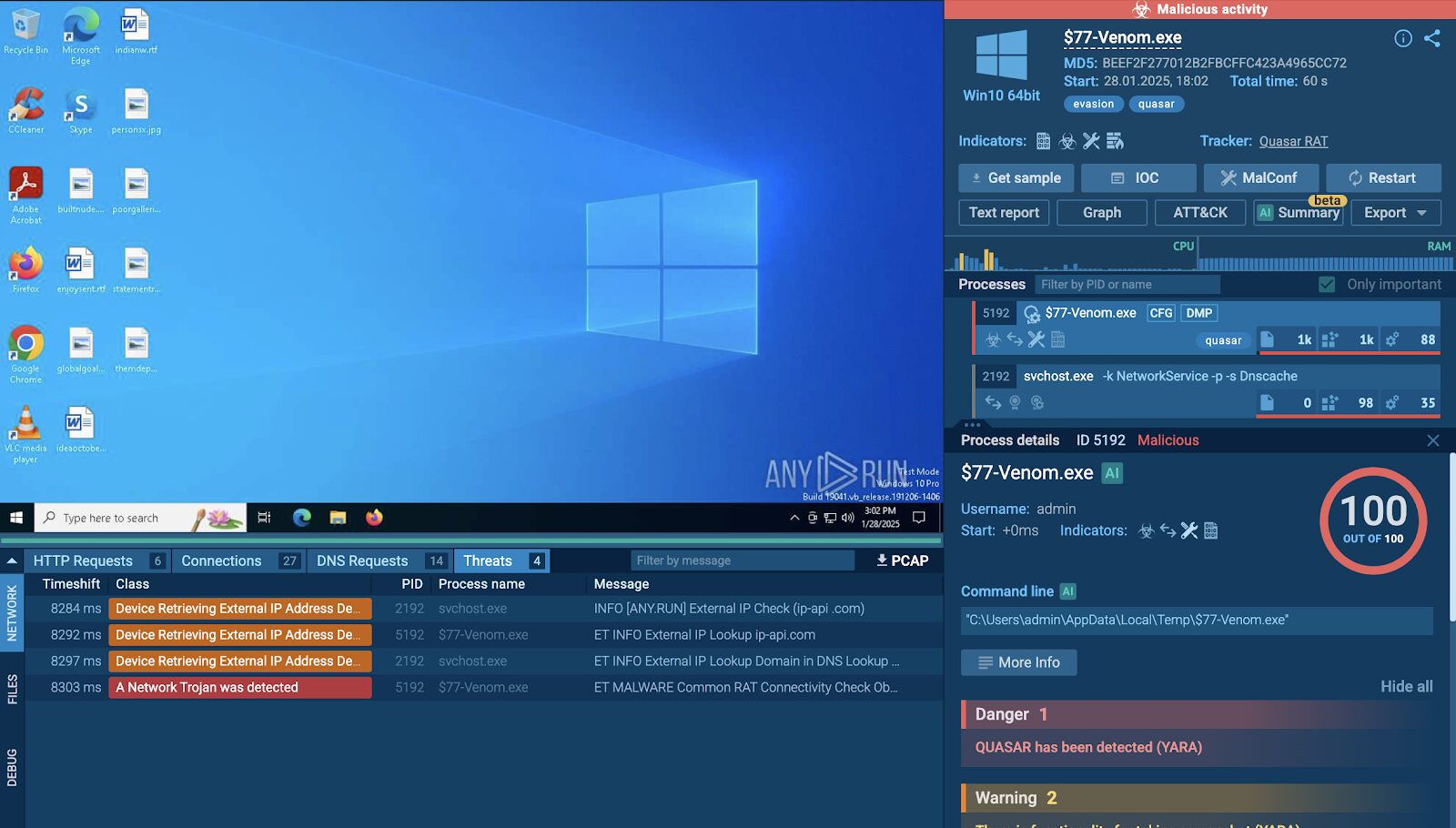
Quasar RAT analysis session helps understand how the malware works
The Sandbox is a community-driven database of malware samples in action, detonated in the safe environment of a customizable virtual machine. Every analysis is recorded and can be viewed or re-run with changed parameters in order to understand how a malware would behave in a client infrastructure.
Better Strategic Planning
Business is all about strategy, and proper planning and resource allocation are impossible without actionable data. Threat intelligence helps entrepreneurs plan and assess their security efforts, understand and foresee the changes in the cyber threat landscape, and be ready to react ahead.
The intelligence data must be fresh and constantly updated; that’s why Threat Intelligence Lookups supports subscriptions to search results for any request. It’s a means to keep up with the evolution of threats and keep your security systems up to date as well:
threatName:”asyncrat” AND submissionCountry:”de”
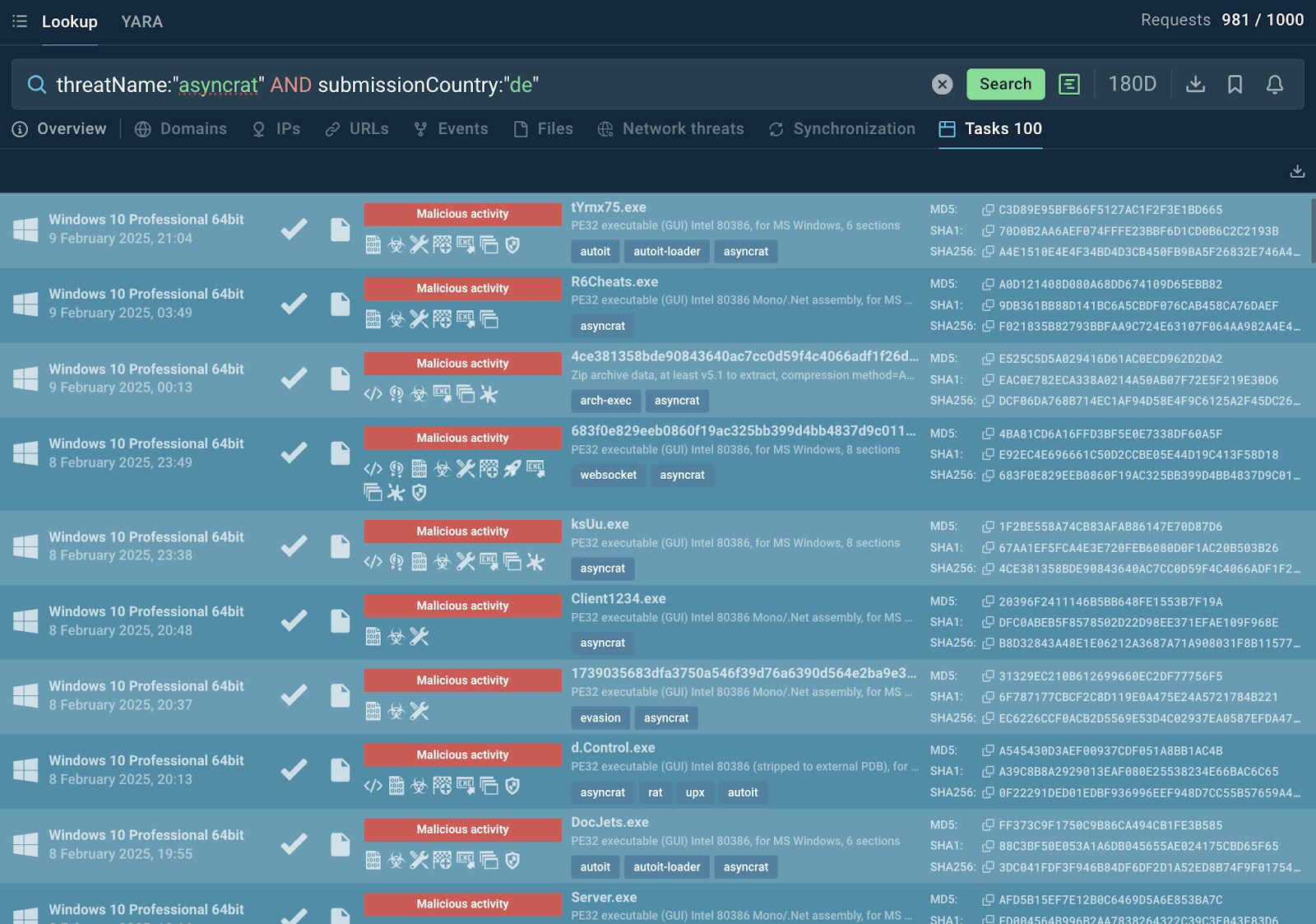
AsyncRAT attack samples added in the Sandbox by German users
This search query is composed to select the latest samples of AsyncRAT attacks analyzed in the Interactive Sandbox by users from Germany. Thus, an organization from Germany can find out whether AsyncRAT is prone to targeting entities from their country, and what industries are especially vulnerable. The results of the research are to be used for prioritizing certain threats and the means of countering.
Conclusion
A successful cyber attack promises not only operational disruptions and financial losses, but also reputation damage, regulatory issues, and legal claims. Fresh, contextual, constantly updated data on threats is vitally important for managing and mitigating these risks. Non the less important are contemporary tools like ANY.RUN’s LI Lookup for gathering and analyzing this information to extract actionable insights.
| Request a trial and let your team test TI Lookup |