The Domain Name System (DNS) is like the internet’s address book, making it possible for us to find and access websites using easy-to-remember names instead of complex numerical IP addresses. However, because DNS plays such a key role in our online communications, it’s also a prime target for cyber threats. For example, SafeDNS blocks 73 million cyber threats every day. Malware, ransomware, phishing, and more sophisticated forms of cyberattacks like Domain Generation Algorithms (DGA) and DNS tunneling exploit DNS to infiltrate and damage systems.
DNS security is an underrated risk. The technology is structured in a way that allows DNS packets to flow through the network without prior scrutiny. Moreover, DNS activity within networks is rarely monitored, creating a blind spot in cybersecurity.
This is a major oversight, considering that according to EfficientIP‘s 2023 report, 88% of companies suffer a DNS attack every year.
What is inside DNS traffic
DNS traffic is more than just a background process; it’s packed with details that keep our online world running smoothly. Every time you type a web address, your device sends a DNS query packed with all sorts of parameters to a DNS server. These might include what kind of request you’re making, the server’s response code, how long a record should stay in the cache (TTL), and even a unique transaction identifier to keep things sorted. DNS queries are essential components of DNS traffic, involving requests made by clients to DNS servers to resolve domain names into IP addresses.
DNS traffic does a lot more than just connect you to websites. Every DNS packet can carry very useful information, such as IP addresses of DNS servers, information on network traffic, the setup and location of domains, and so much more; this information proves very vital in ensuring everything works efficiently and stays safe.
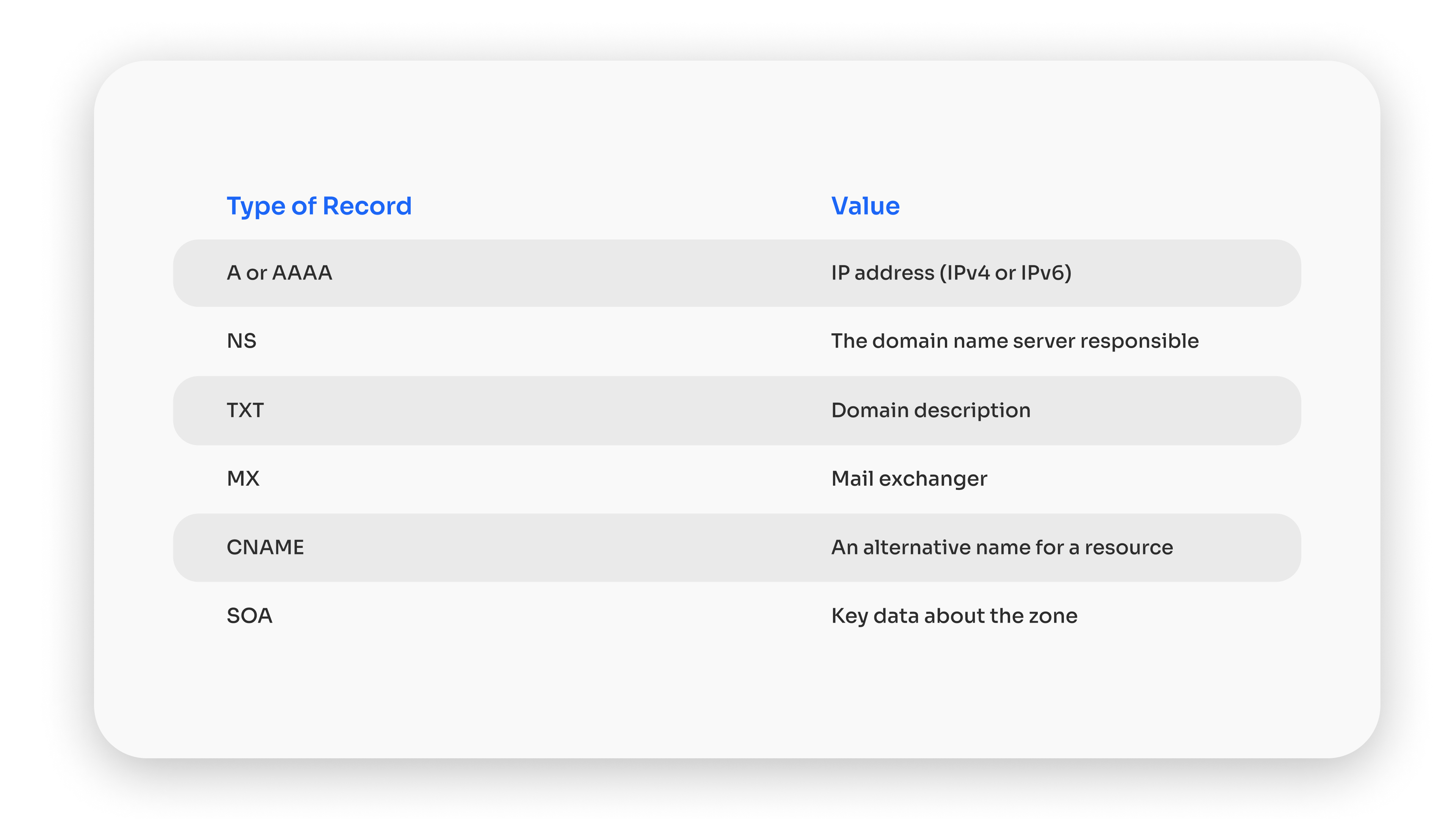
Here is a list of the main parameters:
Threats at the DNS level
Malware
Malicious software, or malware, represents a range of cyber threats including viruses, trojans, spyware, and adware. One particularly dangerous technique is DNS cache poisoning, where malware exploits DNS vulnerabilities to redirect users to harmful sites.It can cause significant
issues, from minor annoyances to major financial losses, by altering browser settings, using up computing resources, and collecting sensitive user data like passwords and credit card numbers.
DNS protection is crucial in combating malware by:
- Blocking access to malicious domains to prevent malware communication and data breaches.
- Monitoring for abnormal behavior to detect malware presence.
- Providing network activity logs to enhance incident response and mitigate security breaches quickly.
Ransomware
Ransomware is a type of malicious software that locks up a computer’s files by encrypting them, making them completely inaccessible.A cyber threat that can hit any individual or large firm, this usually leads to data breaches. Such attacks end up with demands from attackers for a ransom in exchange for file decryption, something which may seriously affect both personal and
business lives.
DNS protection aids against ransomware by:
- Blocking access to ransomware’s command and control servers to disrupt its communication.
- Preventing devices from connecting to malicious websites and email attachments that could initiate an attack.
- Enabling rapid, automated threat detection and alerts, facilitating a swift response to potential ransomware activity.
Phishing and Typosquatting
Phishing and typosquatting are cyber tricks aimed at eliciting sensitive information from individuals through phishing sites or misspelled domain names. DNS spoofing is the hack whereby DNS records are modified by hackers to redirect users to fraudulent sites for malignant purposes like phishing, malware distribution, or disruptions in service.
These practices can compromise personal and corporate security, leading to financial losses and reputational damage.
DNS protection helps combat these threats by:
- Preventing access to fake websites designed to mimic legitimate ones, safeguarding user credentials.
- Utilizing algorithms to identify and block deceitful domains that resemble legitimate sites, protecting users from fraud.
Botnet, Cryptojacking, and C2C
Botnets are the networks formed by a number of internet-connected devices that get infected with malware. They can perform various malicious activities, such as launching DDoS attacks and stealing data, and even illegally mining cryptocurrency. This can wreak havoc not only on energy use and productivity but on financial and reputation issues.
DNS protection helps by:
- Blocking access to known command and control (C&C) servers to disrupt botnet communications.
- Detecting and preventing connections to suspicious domains associated with botnets or C&C servers.
- Identifying unusual patterns that may indicate botnet presence to prevent system infections.
Parked Domains
These domain registrations are sitting on DNS servers that offer parking services—they’re not actively in use but could suddenly host shady stuff on a remote server.
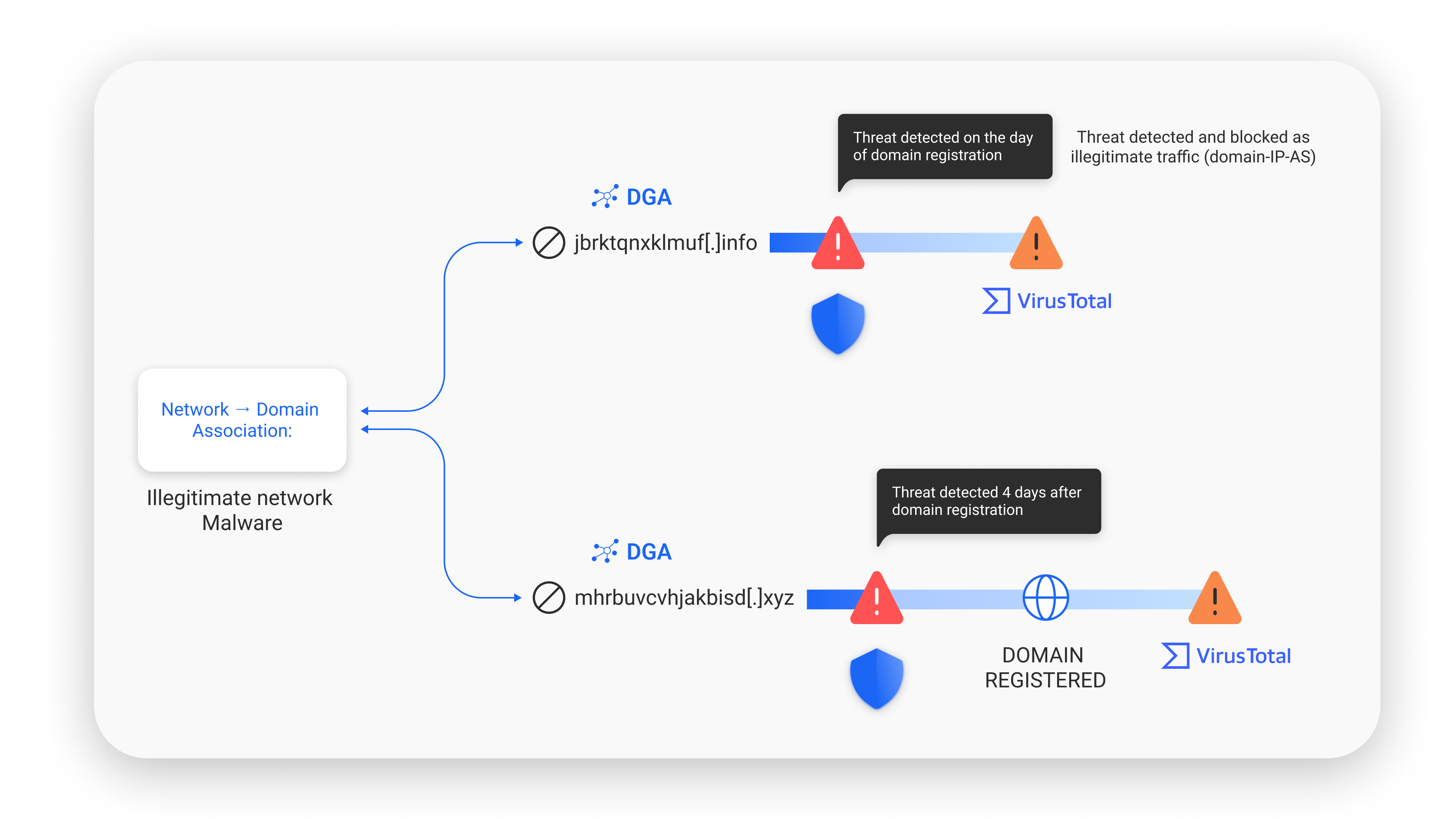
SafeDNS implements a verification pipeline using real-time data from various sources to monitor new domains and their content, identifying and filtering out illegitimate resources at an early stage. The system establishes domain-IP-autonomous system (AS) relationships, which helps in the early detection of malicious domains.
DGA and DNS Tunneling Attacks
DGAs, for Domain Generation Algorithms, come up with mountains of domain lists to keep botnets chattering and bypass security. It doesn’t directly destroy networks, but it does make it easier for crumbling, gnarly software to get in and stay in. That can be big trouble for business networks messing up operations and causing a headache when cleaning up is required.
DNS protection contributes by:
- Detecting and blocking DGA-generated domains using machine learning and traffic analysis, ensuring queries are directed to the correct IP address by verifying information with the authoritative DNS server.
- Monitoring and obstructing abnormal DNS activity that could signify DNS tunneling.
- Maintaining a database of known DNS tunnels to block unauthorized connections and data transmission.
An authoritative DNS server is essential because it holds the official and current info about a domain name’s IP address. This makes sure that DNS queries get the right IP address, which is crucial for stopping DNS tunneling and DGA threats.
Threats at the DNS level are a major concern because they can disrupt operations, compromise sensitive data, and damage reputations. However, with the right solutions in place, many of these threats are preventable. SafeDNS is at the forefront of this defense, leveraging the latest advances in AI and machine learning to effectively detect and mitigate threats.
By processing billions of queries every day, SafeDNS provides real-time monitoring and proactive measures to secure networks. The power of SafeDNS lies in its extensive categorization database of over 2 billion URL records, providing unparalleled protection. This approach ensures that SafeDNS supports the identification of existing, emerging, and robust shielding against DNS-level threats. By putting in place SafeDNS, any organization will have gone a step closer to securing an online presence and continuity and integrity of digital assets.



































