With more than two decades of SAP GRC security experience under my belt, I’ve seen firsthand how businesses work with the same issues—repetitive, error-ridden tasks that tie up valuable time, sap resources, and exacerbate compliance risks. From dealing with access requests through tracking key transactions, these are often manpower-consuming, leading to inefficiencies as well as holes in security.
The silver lining: technology has come a long way. Thanks to the capabilities of automation, Chatbots, and AI/ML features, enterprises can now simplify sophisticated security and compliance processes with no room for errors while boosting performance. It is no longer a matter of whether automation can be done but rather how you can harness it to empower your SAP environment.
Let’s examine how SAP Security & GRC can be transformed through automation to change the way businesses protect their systems while remaining forward-thinking regarding threats.
Here is a glimpse of 10 key SAP tasks businesses need to automate, as well as how ToggleNow is enabling organizations with innovative technology.
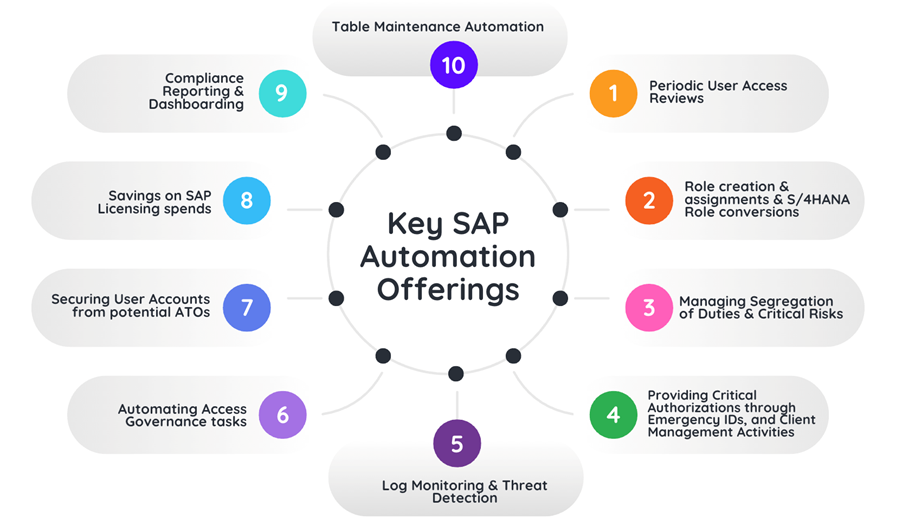
Each of these are explained in the below sections:
1) Periodic User Access Reviews: A Crucial Security Measure
Regular user access reviews are a best practice in maintaining that only the correct users still have access to sensitive systems, eventually preventing insider threats and security breaches. Regular reviews are not just best practices but are also a must to remain compliant with a range of industry standards. The following is an examination of the primary compliance frameworks requiring regular access reviews and why they are important:
- SOX (Sarbanes-Oxley Act): Access controls and recurrent review of users’ access have a strong priority in this bill, especially within financial systems. Recurrent review ensures sensitive information about finances will not be allowed to be viewed by unauthorized sources.
- HIPAA (Health Insurance Portability and Accountability Act): HIPAA demands strict access controls to Protected Health Information (PHI). Although it does not specifically mandate periodic reviews, it does anticipate organizations to ensure access by authorized staff, thus regular reviews are a compliance best practice.
- GDPR (General Data Protection Regulation): Although GDPR does not require periodic reviews to be performed directly, it focuses on data protection by design and need-to-know access. Access reviews on a regular basis conform to these concepts, allowing organizations to maintain compliance with the regulation.
- ISO 27001: This global information security management standard mandates user access management and regular review as part of an overall Information Security Management System (ISMS), assisting organizations in protecting sensitive information by way of controlled access.
- PCI-DSS (Payment Card Industry Data Security Standard): For entities that process cardholder data, PCI-DSS mandates periodic user access review to ensure that only individuals with a need to access payment card data have such access.
2) Role Creation and Assignment: Streamlining SAP Security
SAP role designing and management is usually a tiresome and difficult task for security teams. The pains of maintaining Segregation of Duties (SoD) compliance, handling access requests, and mass role assignment can easily overwhelm teams, especially during system rollout or migrations. The time spent in the manual processes of inferring roles, maintaining authorization objects, and rolling out roles to users not only wastes precious time but also poses the risk of misconfigurations.
Further, companies transitioning to S/4HANA, RISE with SAP, or GROW with SAP have to redesign their models of authorization. The exercise often proves to be cumbersome, technical, and manual, further increasing the workload for security teams, which must ascertain roles and permission match new technology environments and new business processes.
3) SoD (Segregation of Duties) Analysis & Mitigation: Strengthening Internal Controls
Segregation of Duties (SoD) is one of the most fundamental SAP security concepts, put in place to prevent conflict of interest and reduce the chances of fraud, errors, and system abuse. Segregation of important tasks between different users enables organizations to tighten their internal controls, accountability, and monitoring so that no single user can carry out conflicting tasks. SoD management is required to be properly done in order to achieve compliance with audit and regulatory controls, and as such, it forms a critical component of any organization’s security and compliance plans.
4) Providing Critical Authorizations through Emergency IDs and Automating Client Management Activities
Providing secure, time-limited access through Emergency IDs ensures operations remain agile without compromising control. Automating client management activities removes manual effort, reduces errors, and accelerates system tasks. Together, these solutions enhance response times while bolstering security and compliance.
Organizations must carefully define and assign critical authorizations, ensuring they are used properly and reviewed regularly to prevent misuse.
5) SAP License Audit & Optimization
Periodic review and optimization of SAP licenses are essential to prevent surprise penalties, manage costs, and ensure organizations get the best out of their SAP investment. In the absence of proactive license management, companies risk over-licensing—paying for more licenses than they need—or under-utilization, where licenses are underutilized but still paid for. Moreover, organizations put themselves at risk of expensive audit penalties if they don’t manage their licenses effectively. A strategic strategy to license management guarantees complete compliance, reveals concealed savings, and enhances overall operational effectiveness.
The complexity of license management increases during business expansions, mergers, or acquisitions. In these cases, it’s crucial to realign SAP licenses with updated enterprise metrics and structures to reduce financial liabilities and avoid unnecessary costs. Without proper alignment, an organization may face both financial and legal challenges.
6) Securing User Accounts from potential ATOs
According to 2025 Data Breach Investigations Report by Verizon Business, 36% of the breaches are due to system intrusion, where weakly maintained user accounts is one of the reason.
Over 70% of users either utilize weak passwords or fail to update their passwords regularly, a situation that cybersecurity professionals and organizations deem a significant threat. Furthermore, maintaining user accounts and authorizations should be a continuous process for any organization. Compliance teams often find themselves manually pursuing managers for recertifications, resulting in delays and missed deadlines.
7) Automating Access Governance tasks
Most organizations continue to carry out access governance activities manually through spreadsheets, emails, and laborious approvals. This methodology raises the threat of errors, delays, and compliance issues. As businesses expand, manual methods become unsustainable. Access governance needs to be automated to enhance efficiency, strengthen security, and promote consistent compliance.
8) Log Monitoring & Threat Detection
Cyber attacks are becoming more complex, focusing on key business systems such as SAP to exfiltrate information, compromise operations, or inflict economic loss. SAP environments contain confidential data and manage important business processes and, therefore, represent the most appealing targets for malicious attackers. Legacy security is not sufficient anymore. Ongoing log monitoring and sophisticated threat detection are necessary to detect suspicious behavior rapidly, respond to an incident, and maintain the integrity of SAP landscapes.
9) Compliance Reporting & Dashboarding
ITGC (IT General Controls) reporting is often complex due to the need to gather data from multiple systems, validate controls, and ensure complete, accurate documentation. Enterprises typically rely on manual processes—compiling spreadsheets, coordinating with different teams, and cross-checking evidence, which is time-consuming and prone to errors. Generating ITGC reports manually delays audits, increases compliance risks, and strains internal resources. As systems and regulatory requirements grow more complex, manual reporting becomes increasingly unsustainable for enterprises.
10) Simplified Table Maintenance Automation
Managing tables directly in SAP using transactions like SE16, SE16N, or table maintenance Z transaction codes poses significant risks. It’s difficult to control unauthorized changes, and by design, SAP does not allow granular restrictions like permitting only additions while blocking deletions. This lack of control can lead to accidental data loss, integrity issues, and audit concerns, making table access governance critical for SAP GRC security.
Are you still handling these tasks manually? It’s time to embrace AI-powered automation!
With ToggleNow solutions, you can streamline operations, enhance security, and stay ahead of ever-evolving compliance demands. By automating key processes, you free up valuable time and resources, allowing your team to focus on what truly drives your business forward. Say goodbye to manual, error-prone tasks and let AI-powered tools optimize your SAP environment for greater efficiency, compliance, and cost savings.



































